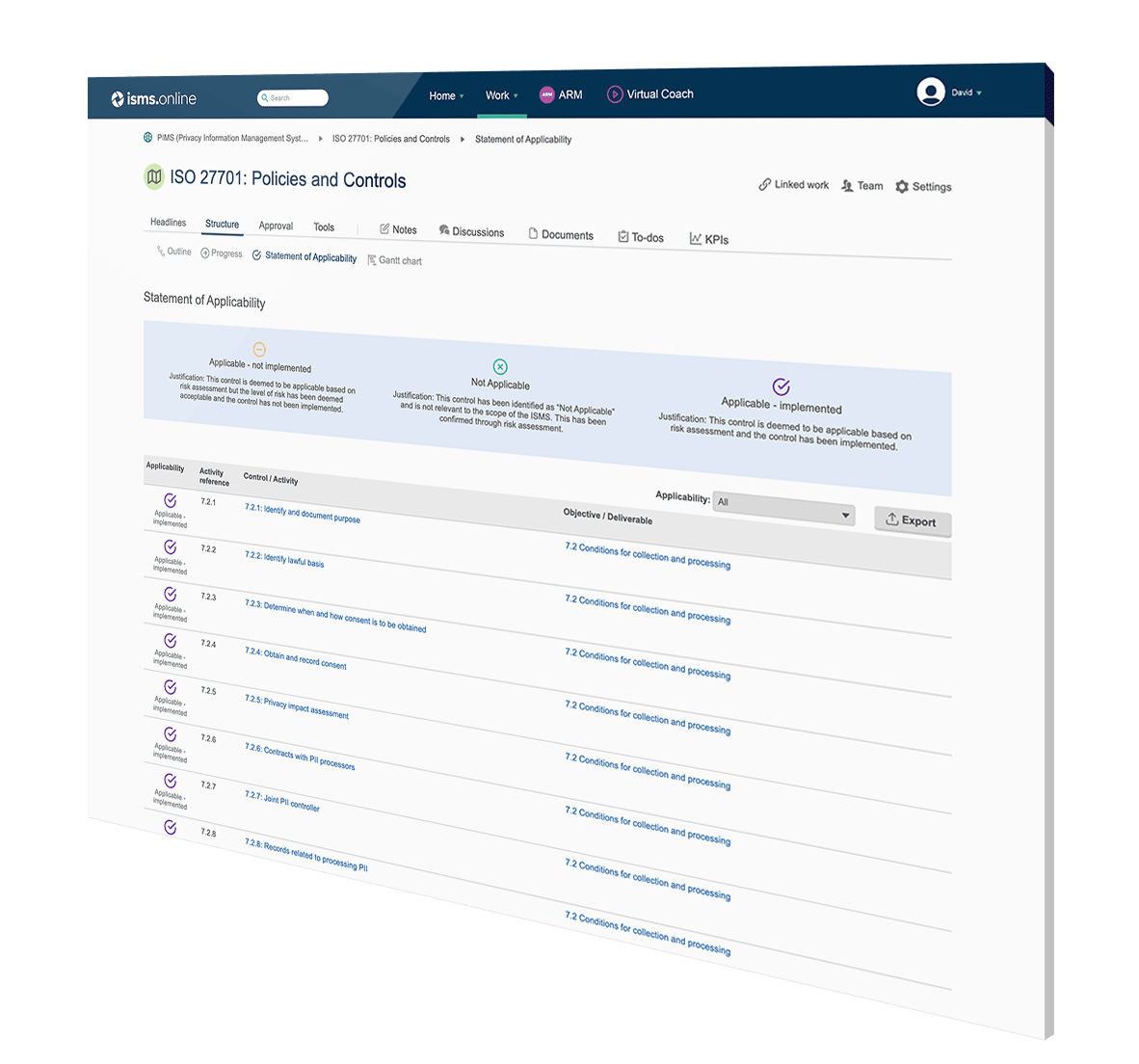
If you have ever done ISO 27001 before, or are some way into your implementation, you’ll know that the Statement of Applicability (SoA) can be a pain point!
External auditors get very excited about this part of the ISMS. It’s easy to fail their expectations as well as waste a huge amount of time in administering and updating it with old fashioned methods offering little real benefit in your day to day operations. ISMS.online is different.
ISMS.online is a sustainable environment and will facilitate the evolution of your organisation.
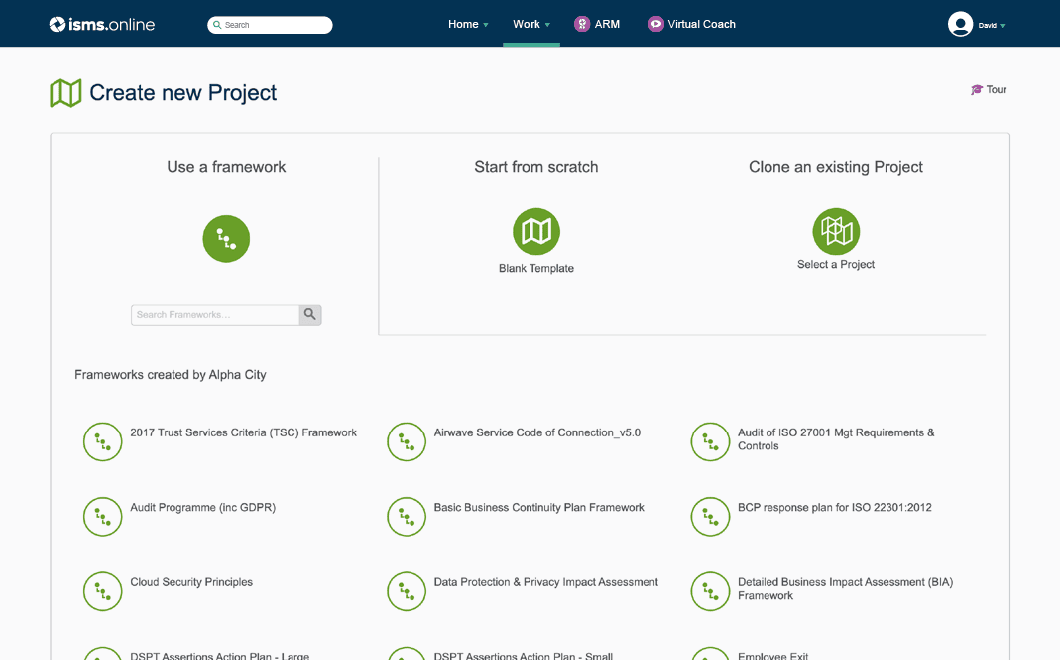

Easily collaborate, create and show you are on top of your documentation at all times
Find out more
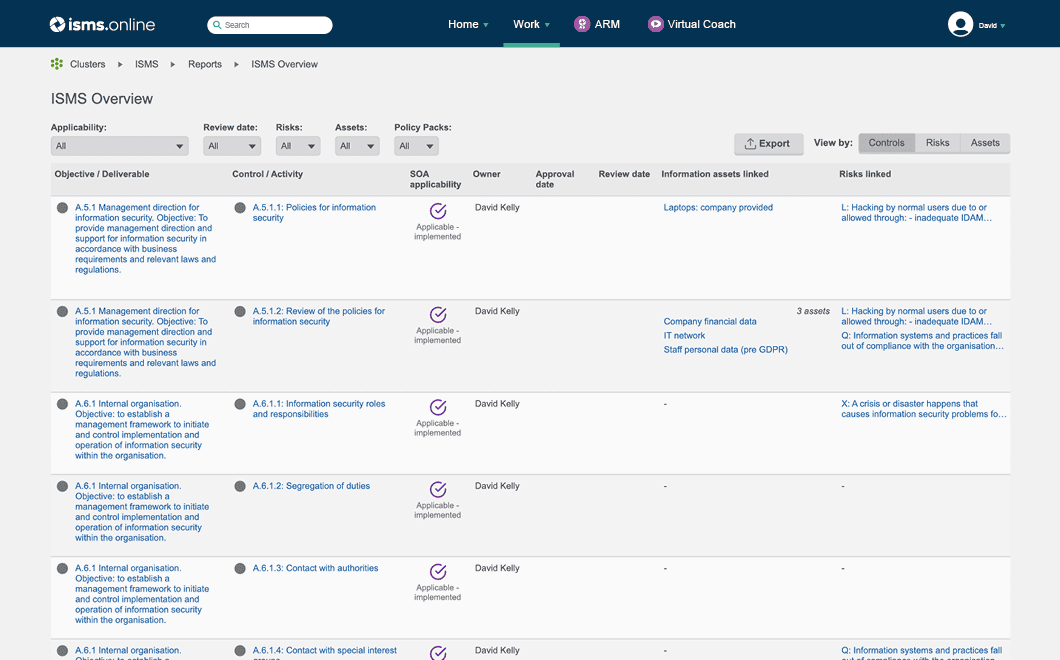
Effortlessly address threats & opportunities and dynamically report on performance
Find out more
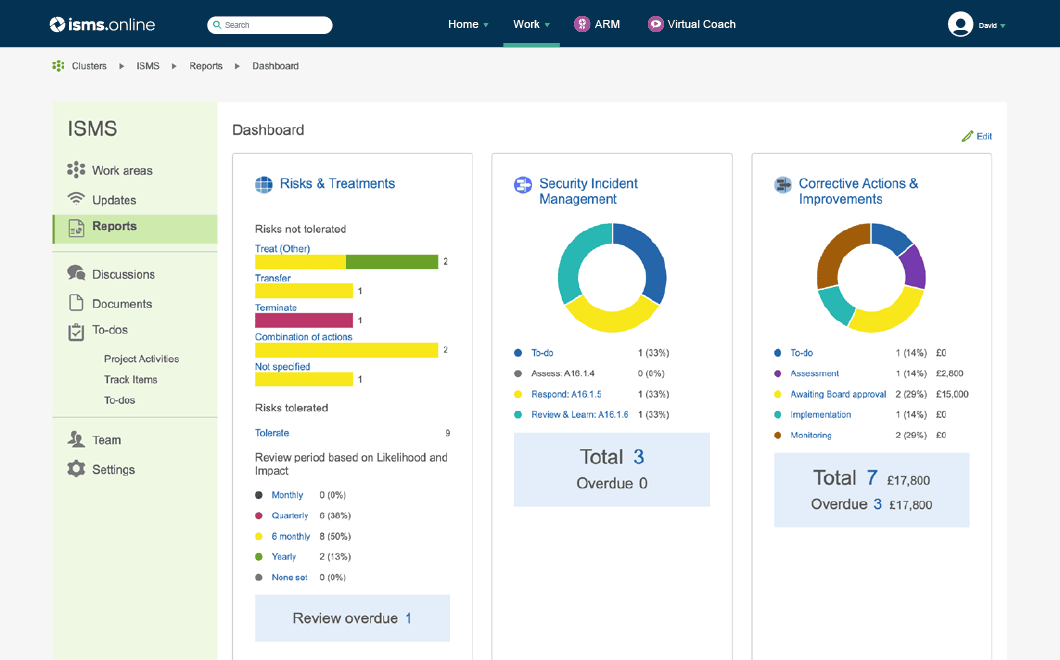
Make better decisions and show you are in control with dashboards, KPIs and related reporting
Find out more
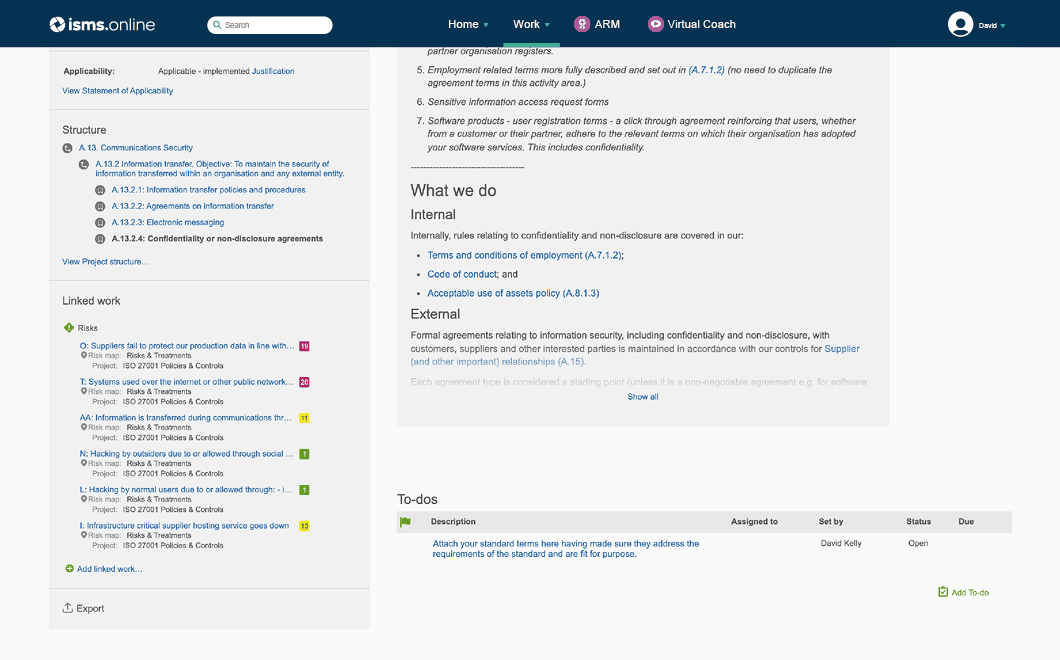
Make light work of corrective actions, improvements, audits and management reviews
Find out more
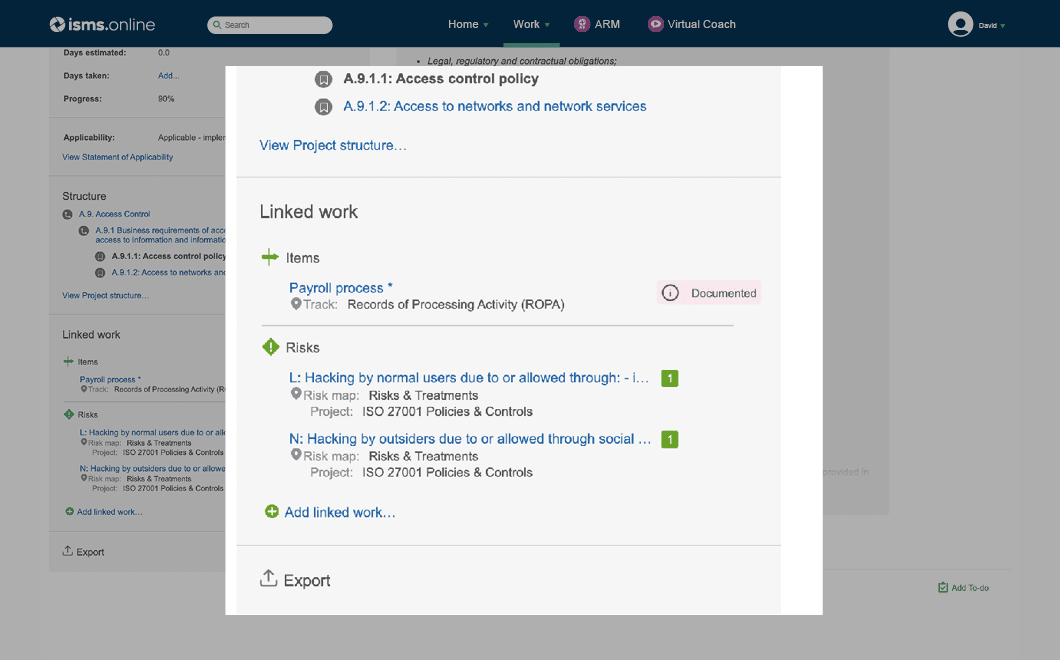
Shine a light on critical relationships and elegantly link areas such as assets, risks, controls and suppliers
Find out moreSelect assets from the Asset Bank and create your Asset Inventory with ease
Find out more
Out of the box integrations with your other key business systems to simplify your compliance
Find out more
Neatly add in other areas of compliance affecting your organisation to achieve even more
Find out more
Engage staff, suppliers and others with dynamic end-to-end compliance at all times
Find out more
Manage due diligence, contracts, contacts and relationships over their lifecycle
Find out more
Visually map and manage interested parties to ensure their needs are clearly addressed
Find out more
Strong privacy by design and security controls to match your needs & expectations
Find out more