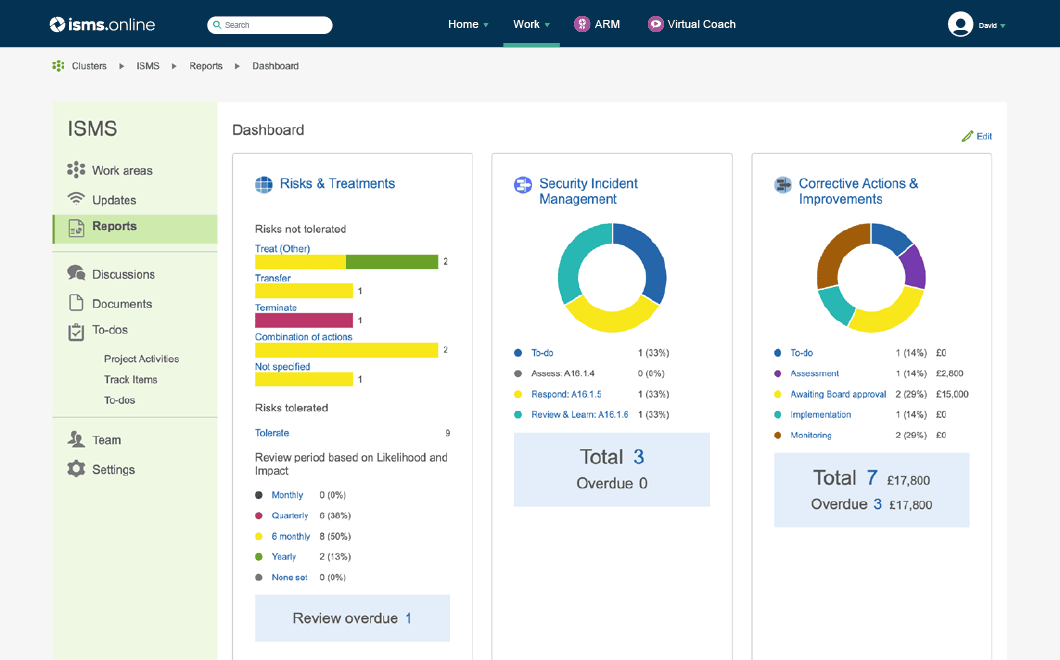
An Information Security Management System (ISMS) describes and demonstrates an organisation’s approach to Information Security (and privacy management). It includes how people, policies, controls and systems identify, then address the opportunities and threats revolving around valuable information and related assets.
Put simply an ISMS is the nerve centre, the holistic point of coordination and control behind the strategic and operational work done to protect and harness valuable information. A good ‘joined up’ professional ISMS shows stakeholders the organisation can be trusted and is serious about its approach to security.
Implemented well and with a business led approach to security, organisations can generate attractive returns on their investment from an ISMS.These include positive growth factors such as helping to win new business as well as mitigating increasing risks in areas such as cyber-crime and privacy regulation.
Privacy is a big topic with regulations like GDPR being front and centre right now. Privacy is not achieved without security therefore a well configured ISMS can help achieve trust in both areas, whereas a privacy management system is generally more limited in its scope. An ISMS delivers a positive return on investment. The goal of our whitepaper is to show you why, what, and how you can get RoI from an ISMS that fits the business needs.