Achieve Robust Information Security with ISO 27001:2022
Our platform empowers your organisation to align with ISO 27001, ensuring comprehensive security management. This international standard is essential for protecting sensitive data and enhancing resilience against cyber threats. With over 70,000 certificates issued globally, ISO 27001's widespread adoption underscores its importance in safeguarding information assets.
Why ISO 27001 Matters
Achieving ISO 27001:2022 certification emphasises a comprehensive, risk-based approach to improving information security management, ensuring your organisation effectively manages and mitigates potential threats, aligning with modern security needs. It provides a systematic methodology for managing sensitive information, ensuring it remains secure. Certification can reduce data breach costs by 30% and is recognised in over 150 countries, enhancing international business opportunities and competitive advantage.
How ISO 27001 Certification Benefits Your Business
-
Achieve Cost Efficiency: Save time and money by preventing costly security breaches. Implement proactive risk management measures to significantly reduce the likelihood of incidents.
-
Accelerate Sales Growth: Streamline your sales process by reducing extensive security documentation requests (RFIs). Showcase your compliance with international information security standards to shorten negotiation times and close deals faster.
-
Boost Client Trust: Demonstrate your commitment to information security to enhance client confidence and build lasting trust. Increase customer loyalty and retain clients in sectors like finance, healthcare, and IT services.
Comprehensive Guide on How to Implement ISO 27001:2022 Certification
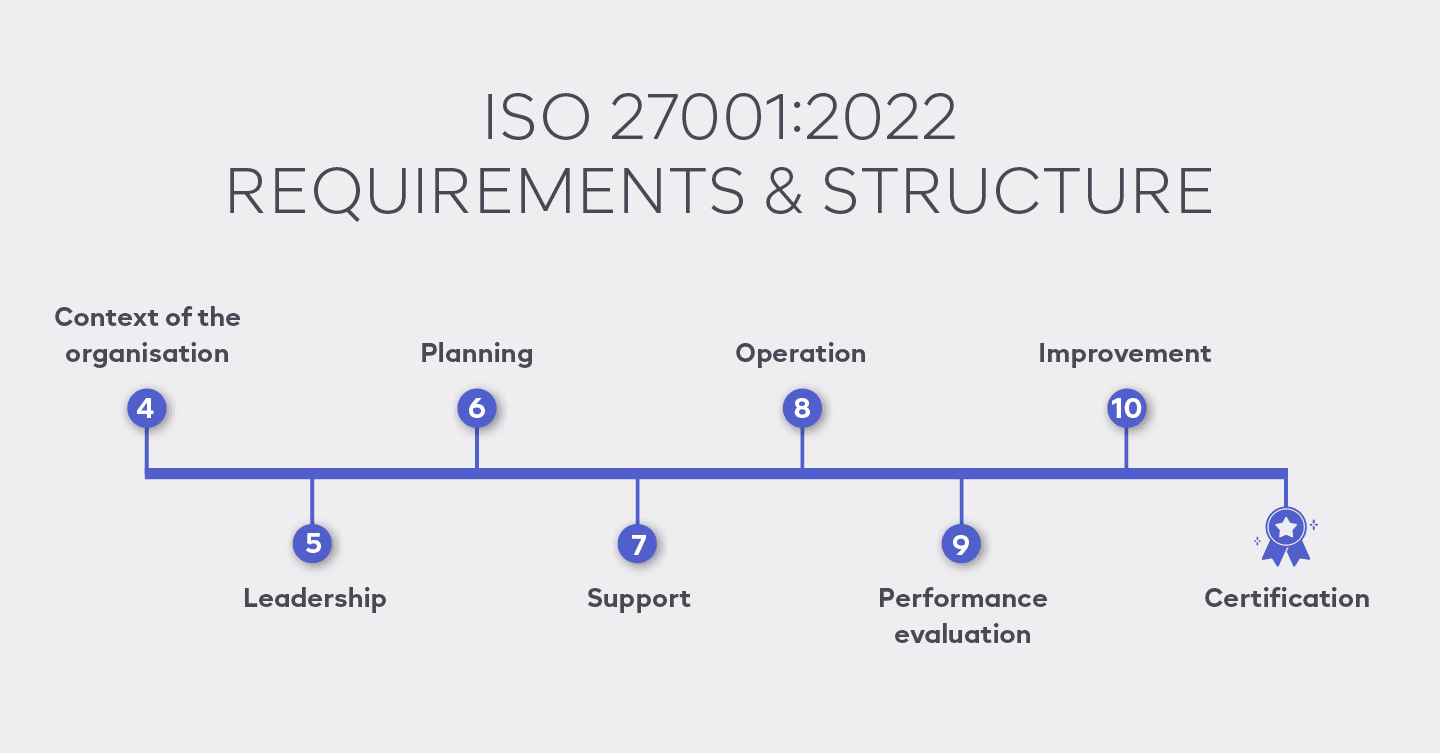
The standard's structure includes a comprehensive Information Security Management System (ISMS) framework and a detailed ISO 27001 implementation guide that integrates risk management processes and Annex A controls. These components create a holistic security strategy, addressing various aspects of security (ISO 27001:2022 Clause 4.2). This approach not only enhances security but also fosters a culture of awareness and compliance within the organisation.
Streamlining Certification with ISMS.online
ISMS.online plays a crucial role in facilitating alignment by offering tools that streamline the certification process. Our platform provides automated risk assessments and real-time monitoring, simplifying the implementation of ISO 27001:2022 requirements. This not only reduces manual effort but also enhances efficiency and accuracy in maintaining alignment.
Join 25000 + Users Achieving ISO 27001 with ISMS.online. Book Your Free Demo Today!
Understanding ISO 27001:2022
ISO 27001 is a pivotal standard for improving an Information Security Management System (ISMS), offering a structured framework to protect sensitive data. This framework integrates comprehensive risk evaluation processes and Annex A controls, forming a robust security strategy. Organisations can effectively identify, analyse, and address vulnerabilities, enhancing their overall security posture.
Key Elements of ISO 27001:2022
-
ISMS Framework: This foundational component establishes systematic policies and procedures for managing information security (ISO 27001:2022 Clause 4.2). It aligns organisational goals with security protocols, fostering a culture of compliance and awareness.
-
Risk Evaluation: Central to ISO 27001, this process involves conducting thorough assessments to identify potential threats. It is essential for implementing appropriate security measures and ensuring continuous monitoring and improvement.
-
ISO 27001 Controls: ISO 27001:2022 outlines a comprehensive set of ISO 27001 controls within Annex A, designed to address various aspects of information security. These controls include measures for access control, cryptography, physical security, and incident management, among others. Implementing these controls ensures your Information Security Management System (ISMS) effectively mitigates risks and safeguards sensitive information.
Aligning with International Standards
ISO 27001:2022 is developed in collaboration with the International Electrotechnical Commission (IEC), ensuring that the standard aligns with global best practices in information security. This partnership enhances the credibility and applicability of ISO 27001 across diverse industries and regions.
How ISO 27001 Integrates with Other Standards
ISO 27001:2022 seamlessly integrates with other standards like ISO 9001 for quality management, ISO 27002 for code of practice for information security controls and regulations like GDPR, enhancing compliance and operational efficiency. This integration allows organisations to streamline regulatory efforts and align security practices with broader business objectives. Initial preparation involves a gap analysis to identify areas needing improvement, followed by a risk evaluation to assess potential threats. Implementing Annex A controls ensures comprehensive security measures are in place. The final audit process, including Stage 1 and Stage 2 audits, verifies compliance and readiness for certification.
Why Is ISO 27001:2022 Important for Organisations?
ISO 27001 plays a vital role in strengthening your organisation's data protection strategies. It provides a comprehensive framework for managing sensitive information, aligning with contemporary cybersecurity requirements through a risk-based approach. This alignment not only fortifies defences but also ensures adherence to regulations like GDPR, mitigating potential legal risks (ISO 27001:2022 Clause 6.1).
ISO 27001:2022 Integration with Other Standards
ISO 27001 is part of the broader ISO family of management system standards. This allows it to be seamlessly integrated with other standards, such as:
- ISO 9001 (Quality Management): Align your quality and information security practices to ensure consistent operational standards across both functions.
- ISO 22301 (Business Continuity): Strengthen your business resilience by integrating security and continuity management into a unified system.
- ISO 27701 (Privacy Information Management): Protect personal data and ensure GDPR compliance by incorporating ISO 27701 alongside ISO 27001.
This integrated approach helps your organisation maintain robust operational standards, streamlining the certification process and enhancing compliance.
How Does ISO 27001:2022 Enhance Risk Management?
- Structured Risk Management: The standard emphasises the systematic identification, assessment, and mitigation of risks, fostering a proactive security posture.
- Incident Reduction: Organisations experience fewer breaches due to the robust controls outlined in Annex A.
- Operational Efficiency: Streamlined processes enhance efficiency, reducing the likelihood of costly incidents.
Structured Risk Management with ISO 27001:2022
ISO 27001 requires organisations to adopt a comprehensive, systematic approach to risk management. This includes:
- Risk Identification and Assessment: Identify potential threats to sensitive data and evaluate the severity and likelihood of those risks (ISO 27001:2022 Clause 6.1).
- Risk Treatment: Select appropriate treatment options, such as mitigating, transferring, avoiding, or accepting risks. With the addition of new options like exploiting and enhancing, organisations can take calculated risks to harness opportunities.
Each of these steps must be reviewed regularly to ensure that the risk landscape is continuously monitored and mitigated as necessary.
What Are the Benefits for Trust and Reputation?
Certification signifies a commitment to data protection, enhancing your business reputation and customer trust. Certified organisations often see a 20% increase in customer satisfaction, as clients appreciate the assurance of secure data handling.
How ISO 27001 Certification Impacts Client Trust and Sales
-
Increased Client Confidence: When prospective clients see that your organisation is ISO 27001 certified, it automatically elevates their trust in your ability to protect sensitive information. This trust is essential for sectors where data security is a deciding factor, such as healthcare, finance, and government contracting.
-
Faster Sales Cycles: ISO 27001 certification reduces the time spent answering security questionnaires during the procurement process. Prospective clients will see your certification as a guarantee of high security standards, speeding up decision-making.
-
Competitive Advantage: ISO 27001 certification positions your company as a leader in information security, giving you an edge over competitors who may not hold this certification.
How Does ISO 27001:2022 Offer Competitive Advantages?
ISO 27001 opens international business opportunities, recognised in over 150 countries. It cultivates a culture of security awareness, positively influencing organisational culture and encouraging continuous improvement and resilience, essential for thriving in today's digital environment.
How Can ISO 27001 Support Regulatory Adherence?
Aligning with ISO 27001 helps navigate complex regulatory landscapes, ensuring adherence to various legal requirements. This alignment reduces potential legal liabilities and enhances overall governance.
Incorporating ISO 27001:2022 into your organisation not only strengthens your data protection framework but also builds a foundation for sustainable growth and trust in the global market.
Get your guide to
ISO 27001 success
Everything you need to know about achieving ISO 27001 first time
Get your free guideEnhancing Risk Management with ISO 27001:2022
ISO 27001:2022 offers a robust framework for managing information security risks, vital for safeguarding your organisation's sensitive data. This standard emphasises a systematic approach to risk evaluation, ensuring potential threats are identified, assessed, and mitigated effectively.
How Does ISO 27001 Structure Risk Management?
ISO 27001:2022 integrates risk evaluation into the Information Security Management System (ISMS), involving:
- Risk Assessment: Conducting thorough evaluations to identify and analyse potential threats and vulnerabilities (ISO 27001:2022 Clause 6.1).
- Risk Treatment: Implementing strategies to mitigate identified risks, using controls outlined in Annex A to reduce vulnerabilities and threats.
- Continuous Monitoring: Regularly reviewing and updating practices to adapt to evolving threats and maintain security effectiveness.
What Techniques and Strategies Are Key?
Effective risk management under ISO 27001:2022 involves:
- Risk Assessment and Analysis: Utilising methodologies like SWOT analysis and threat modelling to evaluate risks comprehensively.
- Risk Treatment and Mitigation: Applying controls from Annex A to address specific risks, ensuring a proactive approach to security.
- Continuous Improvement: Fostering a security-focused culture that encourages ongoing evaluation and enhancement of risk management practices.
How Can the Framework Be Tailored to Your Organisation?
ISO 27001:2022's framework can be customised to fit your organisation's specific needs, ensuring that security measures align with business objectives and regulatory requirements. By fostering a culture of proactive risk management, organisations with ISO 27001 certification experience fewer security breaches and enhanced resilience against cyber threats. This approach not only protects your data but also builds trust with stakeholders, enhancing your organisation's reputation and competitive edge.
Key Changes in ISO 27001:2022
ISO 27001:2022 introduces pivotal updates, enhancing its role in modern cybersecurity. The most significant changes reside in Annex A, which now includes advanced measures for digital security and proactive threat management. These revisions address the evolving nature of security challenges, particularly the increasing reliance on digital platforms.
Key Differences Between ISO 27001:2022 and Earlier Versions
The differences between the 2013 and 2022 versions of ISO 27001 are crucial to understanding the updated standard. While there are no massive overhauls, the refinements in Annex A controls and other areas ensure the standard remains relevant to modern cybersecurity challenges. Key changes include:
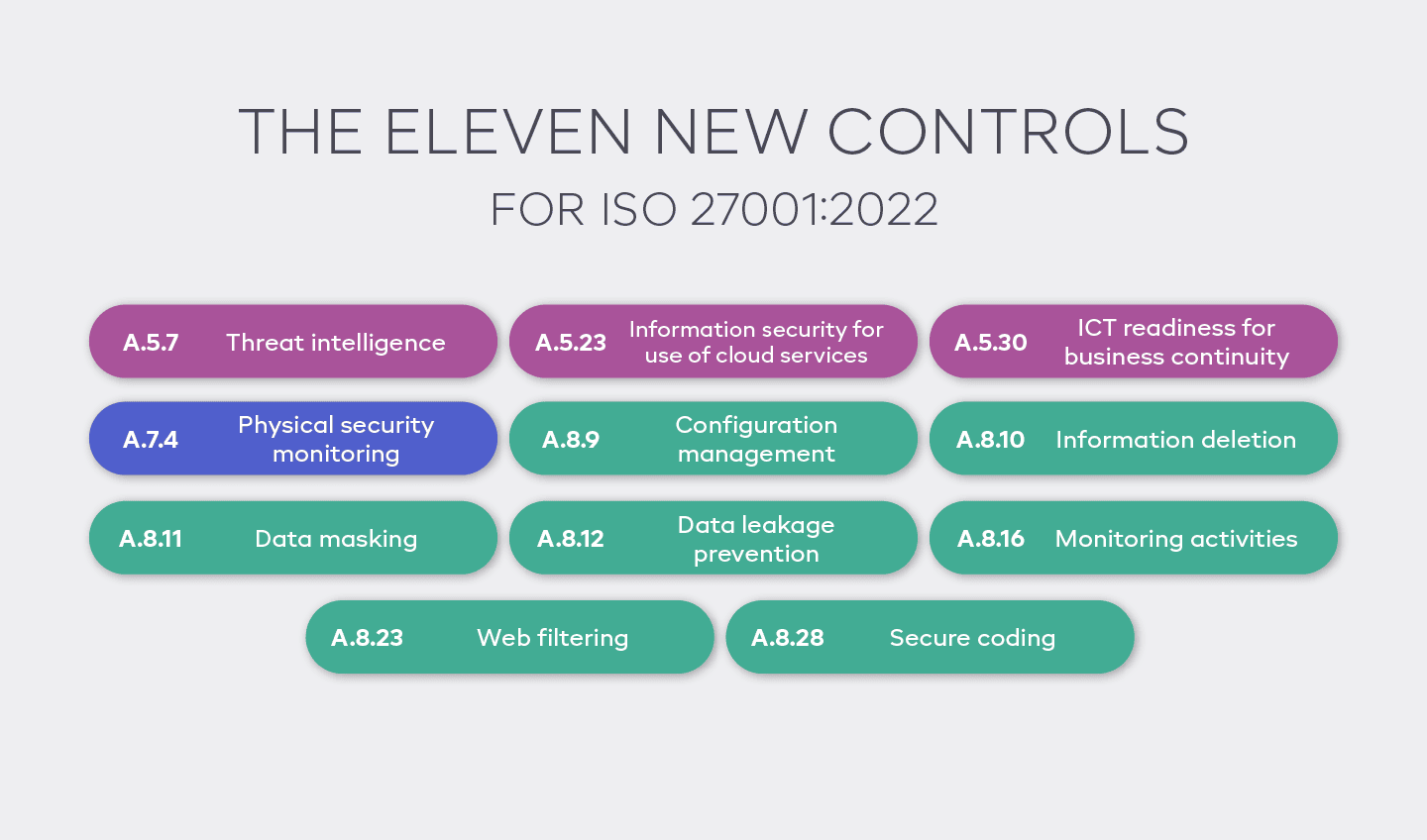
- Restructuring of Annex A Controls: Annex A controls have been condensed from 114 to 93, with some being merged, revised, or newly added. These changes reflect the current cybersecurity environment, making controls more streamlined and focused.
- New Focus Areas: The 11 new controls introduced in ISO 27001:2022 include areas such as threat intelligence, physical security monitoring, secure coding, and cloud service security, addressing the rise of digital threats and the increased reliance on cloud-based solutions.
Understanding Annex A Controls
- Enhanced Security Protocols: Annex A now features 93 controls, with new additions focusing on digital security and proactive threat management. These controls are designed to mitigate emerging risks and ensure robust protection of information assets.
- Digital Security Focus: As digital platforms become integral to operations, ISO 27001:2022 emphasises securing digital environments, ensuring data integrity, and safeguarding against unauthorised access.
- Proactive Threat Management: New controls enable organisations to anticipate and respond to potential security incidents more effectively, strengthening their overall security posture.
Detailed Breakdown of Annex A Controls in ISO 27001:2022
ISO 27001:2022 introduces a revised set of Annex A controls, reducing the total from 114 to 93 and restructuring them into four main groups. Here’s a breakdown of the control categories:
| Control Group | Number of Controls | Examples |
|---|---|---|
| Organisational | 37 | Threat intelligence, ICT readiness, information security policies |
| People | 8 | Responsibilities for security, screening |
| Physical | 14 | Physical security monitoring, equipment protection |
| Technological | 34 | Web filtering, secure coding, data leakage prevention |
New Controls: ISO 27001:2022 introduces 11 new controls focused on emerging technologies and challenges, including:
- Cloud services: Security measures for cloud infrastructure.
- Threat intelligence: Proactive identification of security threats.
- ICT readiness: Business continuity preparations for ICT systems.
By implementing these controls, organisations ensure they are equipped to handle modern information security challenges.
Full Table of ISO 27001 Controls
Below is a full list of ISO 27001:2022 controls
ISO 27001:2022 Organisational Controls
| Annex A Control Type | ISO/IEC 27001:2022 Annex A Identifier | ISO/IEC 27001:2013 Annex A Identifier | Annex A Name |
|---|---|---|---|
| Organisational Controls | Annex A 5.1 | Annex A 5.1.1 Annex A 5.1.2 | Policies for Information Security |
| Organisational Controls | Annex A 5.2 | Annex A 6.1.1 | Information Security Roles and Responsibilities |
| Organisational Controls | Annex A 5.3 | Annex A 6.1.2 | Segregation of Duties |
| Organisational Controls | Annex A 5.4 | Annex A 7.2.1 | Management Responsibilities |
| Organisational Controls | Annex A 5.5 | Annex A 6.1.3 | Contact With Authorities |
| Organisational Controls | Annex A 5.6 | Annex A 6.1.4 | Contact With Special Interest Groups |
| Organisational Controls | Annex A 5.7 | NEW | Threat Intelligence |
| Organisational Controls | Annex A 5.8 | Annex A 6.1.5 Annex A 14.1.1 | Information Security in Project Management |
| Organisational Controls | Annex A 5.9 | Annex A 8.1.1 Annex A 8.1.2 | Inventory of Information and Other Associated Assets |
| Organisational Controls | Annex A 5.10 | Annex A 8.1.3 Annex A 8.2.3 | Acceptable Use of Information and Other Associated Assets |
| Organisational Controls | Annex A 5.11 | Annex A 8.1.4 | Return of Assets |
| Organisational Controls | Annex A 5.12 | Annex A 8.2.1 | Classification of Information |
| Organisational Controls | Annex A 5.13 | Annex A 8.2.2 | Labelling of Information |
| Organisational Controls | Annex A 5.14 | Annex A 13.2.1 Annex A 13.2.2 Annex A 13.2.3 | Information Transfer |
| Organisational Controls | Annex A 5.15 | Annex A 9.1.1 Annex A 9.1.2 | Access Control |
| Organisational Controls | Annex A 5.16 | Annex A 9.2.1 | Identity Management |
| Organisational Controls | Annex A 5.17 | Annex A 9.2.4 Annex A 9.3.1 Annex A 9.4.3 | Authentication Information |
| Organisational Controls | Annex A 5.18 | Annex A 9.2.2 Annex A 9.2.5 Annex A 9.2.6 | Access Rights |
| Organisational Controls | Annex A 5.19 | Annex A 15.1.1 | Information Security in Supplier Relationships |
| Organisational Controls | Annex A 5.20 | Annex A 15.1.2 | Addressing Information Security Within Supplier Agreements |
| Organisational Controls | Annex A 5.21 | Annex A 15.1.3 | Managing Information Security in the ICT Supply Chain |
| Organisational Controls | Annex A 5.22 | Annex A 15.2.1 Annex A 15.2.2 | Monitoring, Review and Change Management of Supplier Services |
| Organisational Controls | Annex A 5.23 | NEW | Information Security for Use of Cloud Services |
| Organisational Controls | Annex A 5.24 | Annex A 16.1.1 | Information Security Incident Management Planning and Preparation |
| Organisational Controls | Annex A 5.25 | Annex A 16.1.4 | Assessment and Decision on Information Security Events |
| Organisational Controls | Annex A 5.26 | Annex A 16.1.5 | Response to Information Security Incidents |
| Organisational Controls | Annex A 5.27 | Annex A 16.1.6 | Learning From Information Security Incidents |
| Organisational Controls | Annex A 5.28 | Annex A 16.1.7 | Collection of Evidence |
| Organisational Controls | Annex A 5.29 | Annex A 17.1.1 Annex A 17.1.2 Annex A 17.1.3 | Information Security During Disruption |
| Organisational Controls | Annex A 5.30 | NEW | ICT Readiness for Business Continuity |
| Organisational Controls | Annex A 5.31 | Annex A 18.1.1 Annex A 18.1.5 | Legal, Statutory, Regulatory and Contractual Requirements |
| Organisational Controls | Annex A 5.32 | Annex A 18.1.2 | Intellectual Property Rights |
| Organisational Controls | Annex A 5.33 | Annex A 18.1.3 | Protection of Records |
| Organisational Controls | Annex A 5.34 | Annex A 18.1.4 | Privacy and Protection of PII |
| Organisational Controls | Annex A 5.35 | Annex A 18.2.1 | Independent Review of Information Security |
| Organisational Controls | Annex A 5.36 | Annex A 18.2.2 Annex A 18.2.3 | Compliance With Policies, Rules and Standards for Information Security |
| Organisational Controls | Annex A 5.37 | Annex A 12.1.1 | Documented Operating Procedures |
ISO 27001:2022 People Controls
| Annex A Control Type | ISO/IEC 27001:2022 Annex A Identifier | ISO/IEC 27001:2013 Annex A Identifier | Annex A Name |
|---|---|---|---|
| People Controls | Annex A 6.1 | Annex A 7.1.1 | Screening |
| People Controls | Annex A 6.2 | Annex A 7.1.2 | Terms and Conditions of Employment |
| People Controls | Annex A 6.3 | Annex A 7.2.2 | Information Security Awareness, Education and Training |
| People Controls | Annex A 6.4 | Annex A 7.2.3 | Disciplinary Process |
| People Controls | Annex A 6.5 | Annex A 7.3.1 | Responsibilities After Termination or Change of Employment |
| People Controls | Annex A 6.6 | Annex A 13.2.4 | Confidentiality or Non-Disclosure Agreements |
| People Controls | Annex A 6.7 | Annex A 6.2.2 | Remote Working |
| People Controls | Annex A 6.8 | Annex A 16.1.2 Annex A 16.1.3 | Information Security Event Reporting |
ISO 27001:2022 Physical Controls
| Annex A Control Type | ISO/IEC 27001:2022 Annex A Identifier | ISO/IEC 27001:2013 Annex A Identifier | Annex A Name |
|---|---|---|---|
| Physical Controls | Annex A 7.1 | Annex A 11.1.1 | Physical Security Perimeters |
| Physical Controls | Annex A 7.2 | Annex A 11.1.2 Annex A 11.1.6 | Physical Entry |
| Physical Controls | Annex A 7.3 | Annex A 11.1.3 | Securing Offices, Rooms and Facilities |
| Physical Controls | Annex A 7.4 | NEW | Physical Security Monitoring |
| Physical Controls | Annex A 7.5 | Annex A 11.1.4 | Protecting Against Physical and Environmental Threats |
| Physical Controls | Annex A 7.6 | Annex A 11.1.5 | Working In Secure Areas |
| Physical Controls | Annex A 7.7 | Annex A 11.2.9 | Clear Desk and Clear Screen |
| Physical Controls | Annex A 7.8 | Annex A 11.2.1 | Equipment Siting and Protection |
| Physical Controls | Annex A 7.9 | Annex A 11.2.6 | Security of Assets Off-Premises |
| Physical Controls | Annex A 7.10 | Annex A 8.3.1 Annex A 8.3.2 Annex A 8.3.3 Annex A 11.2.5 | Storage Media |
| Physical Controls | Annex A 7.11 | Annex A 11.2.2 | Supporting Utilities |
| Physical Controls | Annex A 7.12 | Annex A 11.2.3 | Cabling Security |
| Physical Controls | Annex A 7.13 | Annex A 11.2.4 | Equipment Maintenance |
| Physical Controls | Annex A 7.14 | Annex A 11.2.7 | Secure Disposal or Re-Use of Equipment |
ISO 27001:2022 Technological Controls
| Annex A Control Type | ISO/IEC 27001:2022 Annex A Identifier | ISO/IEC 27001:2013 Annex A Identifier | Annex A Name |
|---|---|---|---|
| Technological Controls | Annex A 8.1 | Annex A 6.2.1 Annex A 11.2.8 | User Endpoint Devices |
| Technological Controls | Annex A 8.2 | Annex A 9.2.3 | Privileged Access Rights |
| Technological Controls | Annex A 8.3 | Annex A 9.4.1 | Information Access Restriction |
| Technological Controls | Annex A 8.4 | Annex A 9.4.5 | Access to Source Code |
| Technological Controls | Annex A 8.5 | Annex A 9.4.2 | Secure Authentication |
| Technological Controls | Annex A 8.6 | Annex A 12.1.3 | Capacity Management |
| Technological Controls | Annex A 8.7 | Annex A 12.2.1 | Protection Against Malware |
| Technological Controls | Annex A 8.8 | Annex A 12.6.1 Annex A 18.2.3 | Management of Technical Vulnerabilities |
| Technological Controls | Annex A 8.9 | NEW | Configuration Management |
| Technological Controls | Annex A 8.10 | NEW | Information Deletion |
| Technological Controls | Annex A 8.11 | NEW | Data Masking |
| Technological Controls | Annex A 8.12 | NEW | Data Leakage Prevention |
| Technological Controls | Annex A 8.13 | Annex A 12.3.1 | Information Backup |
| Technological Controls | Annex A 8.14 | Annex A 17.2.1 | Redundancy of Information Processing Facilities |
| Technological Controls | Annex A 8.15 | Annex A 12.4.1 Annex A 12.4.2 Annex A 12.4.3 | Logging |
| Technological Controls | Annex A 8.16 | NEW | Monitoring Activities |
| Technological Controls | Annex A 8.17 | Annex A 12.4.4 | Clock Synchronization |
| Technological Controls | Annex A 8.18 | Annex A 9.4.4 | Use of Privileged Utility Programs |
| Technological Controls | Annex A 8.19 | Annex A 12.5.1 Annex A 12.6.2 | Installation of Software on Operational Systems |
| Technological Controls | Annex A 8.20 | Annex A 13.1.1 | Networks Security |
| Technological Controls | Annex A 8.21 | Annex A 13.1.2 | Security of Network Services |
| Technological Controls | Annex A 8.22 | Annex A 13.1.3 | Segregation of Networks |
| Technological Controls | Annex A 8.23 | NEW | Web filtering |
| Technological Controls | Annex A 8.24 | Annex A 10.1.1 Annex A 10.1.2 | Use of Cryptography |
| Technological Controls | Annex A 8.25 | Annex A 14.2.1 | Secure Development Life Cycle |
| Technological Controls | Annex A 8.26 | Annex A 14.1.2 Annex A 14.1.3 | Application Security Requirements |
| Technological Controls | Annex A 8.27 | Annex A 14.2.5 | Secure System Architecture and Engineering Principles |
| Technological Controls | Annex A 8.28 | NEW | Secure Coding |
| Technological Controls | Annex A 8.29 | Annex A 14.2.8 Annex A 14.2.9 | Security Testing in Development and Acceptance |
| Technological Controls | Annex A 8.30 | Annex A 14.2.7 | Outsourced Development |
| Technological Controls | Annex A 8.31 | Annex A 12.1.4 Annex A 14.2.6 | Separation of Development, Test and Production Environments |
| Technological Controls | Annex A 8.32 | Annex A 12.1.2 Annex A 14.2.2 Annex A 14.2.3 Annex A 14.2.4 | Change Management |
| Technological Controls | Annex A 8.33 | Annex A 14.3.1 | Test Information |
| Technological Controls | Annex A 8.34 | Annex A 12.7.1 | Protection of Information Systems During Audit Testing |
Navigating Implementation Challenges
Organisations may face challenges such as resource constraints and insufficient management support when implementing these updates. Effective resource allocation and stakeholder engagement are crucial for maintaining momentum and achieving successful compliance. Regular training sessions can help clarify the standard's requirements, reducing compliance challenges.
Adapting to Evolving Security Threats
These updates demonstrate ISO 27001:2022's adaptability to the changing security environment, ensuring organisations remain resilient against new threats. By aligning with these enhanced requirements, your organisation can bolster its security framework, improve compliance processes, and maintain a competitive edge in the global market.
How Can Organisations Successfully Attain ISO 27001 Certification?
Achieving ISO 27001:2022 requires a methodical approach, ensuring your organisation aligns with the standard's comprehensive requirements. Here's a detailed guide to navigate this process effectively:
Kickstart Your Certification with a Thorough Gap Analysis
Identify improvement areas with a comprehensive gap analysis. Assess current practices against ISO 27001 standard to pinpoint discrepancies. Develop a detailed project plan outlining objectives, timelines, and responsibilities. Engage stakeholders early to secure buy-in and allocate resources efficiently.
Implement an Effective ISMS
Establish and implement an Information Security Management System (ISMS) tailored to your organisational goals. Implement the 93 Annex A controls, emphasising risk assessment and treatment (ISO 27001:2022 Clause 6.1). Our platform, ISMS.online, automates compliance tasks, reducing manual effort and enhancing precision.
Perform Regular Internal Audits
Conduct regular internal audits to evaluate the effectiveness of your ISMS. Management reviews are essential for performance evaluation and necessary adjustments (ISO 27001:2022 Clause 9.3). ISMS.online facilitates real-time collaboration, boosting team efficiency and audit readiness.
Engage with Certification Bodies
Select an accredited certification body and schedule the audit process, including Stage 1 and Stage 2 audits. Ensure all documentation is complete and accessible. ISMS.online offers templates and resources to simplify documentation and track progress.
Overcome Common Challenges with a Free Consultation
Overcome resource constraints and resistance to change by fostering a culture of security awareness and continuous improvement. Our platform supports maintaining alignment over time, aiding your organisation in achieving and sustaining certification.
Schedule a free consultation to address resource constraints and navigate resistance to change. Learn how ISMS.online can support your implementation efforts and ensure successful certification.
ISO 27001:2022 and Supplier Relationships Requirements
ISO 27001:2022 has introduced new requirements to ensure organisations maintain robust supplier and third-party management programs. This includes:
- Identifying and Assessing Suppliers: Organisations must identify and analyse third-party suppliers that impact information security. A thorough risk assessment for each supplier is mandatory to ensure compliance with your ISMS.
- Supplier Security Controls: Ensure that your suppliers implement adequate security controls and that these are regularly reviewed. This extends to ensuring that customer service levels and personal data protection are not adversely affected.
- Auditing Suppliers: Organisations should audit their suppliers' processes and systems regularly. This aligns with the new ISO 27001:2022 requirements, ensuring that supplier compliance is maintained and that risks from third-party partnerships are mitigated.
Enhanced Employee Cybersecurity Awareness
ISO 27001:2022 continues to emphasise the importance of employee awareness. Implementing policies for ongoing education and training is critical. This approach ensures that your employees are not only aware of security risks but are also capable of actively participating in mitigating those risks.
- Human Error Prevention: Businesses should invest in training programs that aim to prevent human error, one of the leading causes of security breaches.
- Clear Policy Development: Establish clear guidelines for employee conduct regarding data security. This includes awareness programs on phishing, password management, and mobile device security.
- Security Culture: Foster a security-aware culture where employees feel empowered to raise concerns about cybersecurity threats. An environment of openness helps organisations tackle risks before they materialise into incidents.
ISO 27001:2022 Requirements for Human Resource Security
One of the essential refinements in ISO 27001:2022 is its expanded focus on human resource security. This involves:
- Personnel Screening: Clear guidelines for personnel screening before hiring are crucial to ensuring that employees with access to sensitive information meet required security standards.
- Training and Awareness: Ongoing education is required to ensure that staff are fully aware of the organisation's security policies and procedures.
- Disciplinary Actions: Define clear consequences for policy violations, ensuring that all employees understand the importance of complying with security requirements.
These controls ensure that organisations manage both internal and external personnel security risks effectively.
Compliance doesn’t have to be complicated.
We've done the hard work for you, giving you an 81% Headstart from the moment you log on.
All you have to do is fill in the blanks.
Employee Awareness Programs and Security Culture
Fostering a culture of security awareness is crucial for maintaining strong defences against evolving cyber threats. ISO 27001:2022 promotes ongoing training and awareness programs to ensure that all employees, from leadership to staff, are involved in upholding information security standards.
- Phishing Simulations and Security Drills: Conducting regular security drills and phishing simulations helps ensure employees are prepared to handle cyber incidents.
- Interactive Workshops: Engage employees in practical training sessions that reinforce key security protocols, improving overall organisational awareness.
Continual Improvement and Cybersecurity Culture
Finally, ISO 27001:2022 advocates for a culture of continual improvement, where organisations consistently evaluate and update their security policies. This proactive stance is integral to maintaining compliance and ensuring the organisation stays ahead of emerging threats.
- Security Governance: Regular updates to security policies and audits of cybersecurity practices ensure ongoing compliance with ISO 27001:2022.
- Proactive Risk Management: Encouraging a culture that prioritises risk assessment and mitigation allows organisations to stay responsive to new cyber threats.
Optimal Timing for ISO 27001 Adoption
Adopting ISO 27001:2022 is a strategic decision that depends on your organisation's readiness and objectives. The ideal timing often aligns with periods of growth or digital transformation, where enhancing security frameworks can significantly improve business outcomes. Early adoption provides a competitive edge, as certification is recognised in over 150 countries, expanding international business opportunities.
Conducting a Readiness Assessment
To ensure a seamless adoption, conduct a thorough readiness assessment to evaluate current security practices against the updated standard. This involves:
- Gap Analysis: Identify areas needing improvement and align them with ISO 27001:2022 requirements.
- Resource Allocation: Ensure adequate resources, including personnel, technology, and budget, are available to support the adoption.
- Stakeholder Engagement: Secure buy-in from key stakeholders to facilitate a smooth adoption process.
Aligning Certification with Strategic Goals
Aligning certification with strategic goals enhances business outcomes. Consider:
- Timeline and Deadlines: Be aware of industry-specific deadlines for compliance to avoid penalties.
- Continuous Improvement: Foster a culture of ongoing evaluation and enhancement of security practices.
Utilising ISMS.online for Effective Management
Our platform, ISMS.online, plays a vital role in managing the adoption effectively. It offers tools for automating compliance tasks, reducing manual effort, and providing real-time collaboration features. This ensures your organisation can maintain compliance and track progress efficiently throughout the adoption process.
By strategically planning and utilising the right tools, your organisation can navigate the adoption of ISO 27001:2022 smoothly, ensuring robust security and compliance.
Where Does ISO 27001:2022 Align with Other Regulatory Standards?
ISO 27001 plays a significant role in aligning with key regulatory frameworks, such as GDPR and NIS 2, to enhance data protection and streamline regulatory adherence. This alignment not only strengthens data privacy but also improves organisational resilience across multiple frameworks.
How Does ISO 27001:2022 Enhance GDPR Compliance?
ISO 27001:2022 complements GDPR by focusing on data protection and privacy through its comprehensive risk management processes (ISO 27001:2022 Clause 6.1). The standard's emphasis on safeguarding personal data aligns with GDPR's stringent requirements, ensuring robust data protection strategies.
What Role Does ISO 27001:2022 Play in Supporting NIS 2 Directives?
The standard supports NIS 2 directives by enhancing cybersecurity resilience. ISO 27001:2022's focus on threat intelligence and incident response aligns with NIS 2's objectives, fortifying organisations against cyber threats and ensuring continuity of critical services.
How Does ISO 27001:2022 Integrate with Other ISO Standards?
ISO 27001 integrates effectively with other ISO standards, such as ISO 9001 and ISO 14001, creating synergies that enhance overall regulatory alignment and operational efficiency. This integration facilitates a unified approach to managing quality, environmental, and security standards within an organisation.
How Can Organisations Achieve Comprehensive Regulatory Alignment with ISO 27001:2022?
Organisations can achieve comprehensive regulatory alignment by synchronising their security practices with broader requirements. Our platform, ISMS.online, offers extensive certification support, providing tools and resources to simplify the process. Industry associations and webinars further enhance understanding and implementation, ensuring organisations remain compliant and competitive.
Can ISO 27001:2022 Effectively Mitigate New Security Challenges?
Emerging threats, including cyber-attacks and data breaches, necessitate robust strategies. ISO 27001:2022 offers a comprehensive framework for managing risks, emphasising a risk-based approach to identify, assess, and mitigate potential threats.
How Does ISO 27001:2022 Enhance Cyber Threat Mitigation?
ISO 27001:2022 strengthens mitigation through structured risk management processes. By implementing Annex A controls, organisations can proactively address vulnerabilities, reducing cyber incidents. This proactive stance builds trust with clients and partners, differentiating businesses in the market.
What Measures Ensure Cloud Security with ISO 27001:2022?
Cloud security challenges are prevalent as organisations migrate to digital platforms. ISO 27001:2022 includes specific controls for cloud environments, ensuring data integrity and safeguarding against unauthorised access. These measures foster customer loyalty and enhance market share.
How Does ISO 27001:2022 Prevent Data Breaches?
Data breaches pose significant risks, impacting reputation and financial stability. ISO 27001:2022 establishes comprehensive protocols, ensuring continuous monitoring and improvement. Certified organisations often experience fewer breaches, maintaining effective security measures.
How Can Organisations Adapt to Evolving Threat Landscapes?
Organisations can adapt ISO 27001:2022 to evolving threats by regularly updating security practices. This adaptability ensures alignment with emerging threats, maintaining robust defences. By demonstrating a commitment to security, certified organisations gain a competitive edge and are preferred by clients and partners.
Cultivating a Security Culture with ISO 27001 Compliance
ISO 27001 serves as a cornerstone in developing a robust security culture by emphasising awareness and comprehensive training. This approach not only fortifies your organisation’s security posture but also aligns with current cybersecurity standards.
How to Enhance Security Awareness and Training
Security awareness is integral to ISO 27001:2022, ensuring your employees understand their roles in protecting information assets. Tailored training programmes empower staff to recognise and respond to threats effectively, minimising incident risks.
What Are Effective Training Strategies?
Organisations can enhance training by:
- Interactive Workshops: Conduct engaging sessions that reinforce security protocols.
- E-Learning Modules: Provide flexible online courses for continuous learning.
- Simulated Exercises: Implement phishing simulations and incident response drills to test readiness.
How Does Leadership Influence Security Culture?
Leadership plays a pivotal role in embedding a security-focused culture. By prioritising security initiatives and leading by example, management instils responsibility and vigilance throughout the organisation, making security integral to the organisational ethos.
What Are the Long-Term Benefits of Security Awareness?
ISO 27001:2022 offers sustained improvements and risk reduction, enhancing credibility and providing a competitive edge. Organisations report increased operational efficiency and reduced costs, supporting growth and opening new opportunities.
How Does ISMS.online Support Your Security Culture?
Our platform, ISMS.online, aids organisations by offering tools for tracking training progress and facilitating real-time collaboration. This ensures that security awareness is maintained and continuously improved, aligning with ISO 27001:2022's objectives.
We'll guide you every step of the way
Our built-in tool takes you from set-up to certification with a 100% success rate.
Book a demoNavigating Challenges in ISO 27001:2022 Implementation
Implementing ISO 27001:2022 involves overcoming significant challenges, such as managing limited resources and addressing resistance to change. These hurdles must be addressed to achieve certification and enhance your organisation's information security posture.
Identifying Common Implementation Hurdles
Organisations often face difficulties in allocating adequate resources, both financial and human, to meet ISO 27001:2022's comprehensive requirements. Resistance to adopting new security practices can also impede progress, as employees may be hesitant to alter established workflows.
Efficient Resource Management Strategies
To optimise resource management, prioritise tasks based on risk assessment outcomes, focusing on high-impact areas (ISO 27001:2022 Clause 6.1). Our platform, ISMS.online, automates compliance tasks, reducing manual effort and ensuring critical areas receive the necessary attention.
Overcoming Resistance to Change
Effective communication and training are key to mitigating resistance. Engage employees in the implementation process by highlighting the benefits of ISO 27001:2022, such as enhanced data protection and GDPR alignment. Regular training sessions can foster a culture of security awareness and compliance.
Enhancing Implementation with ISMS.online
ISMS.online plays a pivotal role in overcoming these challenges by providing tools that enhance collaboration and streamline documentation. Our platform supports integrated compliance strategies, aligning ISO 27001 with standards like ISO 9001, thereby improving overall efficiency and regulatory adherence. By simplifying the implementation process, ISMS.online helps your organisation achieve and maintain ISO 27001:2022 certification effectively.
ISO 27001 Frequently Asked Questions
What are Key Differences Between ISO 27001:2022 and Earlier Versions
ISO 27001:2022 introduces pivotal updates to meet evolving security demands, enhancing its relevance in today's digital environment. A significant change is the expansion of Annex A controls, now totaling 93, which include new measures for cloud security and threat intelligence. These additions underscore the growing importance of digital ecosystems and proactive threat management.
Impact on Compliance and Certification
The updates in ISO 27001:2022 require adjustments in compliance processes. Your organisation must integrate these new controls into its Information Security Management Systems (ISMS), ensuring alignment with the latest requirements (ISO 27001:2022 Clause 6.1). This integration streamlines certification by providing a comprehensive framework for managing information risks.
New Controls and Their Significance
The introduction of controls focused on cloud security and threat intelligence is noteworthy. These controls help your organisation protect data in complex digital environments, addressing vulnerabilities unique to cloud systems. By implementing these measures, you can enhance your security posture and reduce the risk of data breaches.
Adapting to New Requirements
To adapt to these changes, your organisation should conduct a thorough gap analysis to identify areas needing improvement. This involves assessing current practices against the updated standard, ensuring alignment with new controls. By using platforms like ISMS.online, you can automate compliance tasks, reducing manual effort and enhancing efficiency.
These updates highlight ISO 27001:2022's commitment to addressing contemporary security challenges, ensuring your organisation remains resilient against emerging threats.
Why Should Compliance Officers Prioritise ISO 27001:2022?
ISO 27001:2022 is pivotal for compliance officers seeking to enhance their organisation's information security framework. Its structured methodology for regulatory adherence and risk management is indispensable in today's interconnected environment.
Navigating Regulatory Frameworks
ISO 27001:2022 aligns with global standards like GDPR, providing a comprehensive framework that ensures data protection and privacy. By adhering to its guidelines, you can confidently navigate complex regulatory landscapes, reducing legal risks and enhancing governance (ISO 27001:2022 Clause 6.1).
Proactive Risk Management
The standard's risk-based approach enables organisations to systematically identify, assess, and mitigate risks. This proactive stance minimises vulnerabilities and fosters a culture of continuous improvement, essential for maintaining a robust security posture. Compliance officers can utilise ISO 27001:2022 to implement effective risk treatment strategies, ensuring resilience against emerging threats.
Enhancing Organisational Security
ISO 27001:2022 significantly enhances your organisation's security posture by embedding security practices into core business processes. This integration boosts operational efficiency and builds trust with stakeholders, positioning your organisation as a leader in information security.
Effective Implementation Strategies
Compliance officers can implement ISO 27001:2022 effectively by utilising platforms like ISMS.online, which streamline efforts through automated risk assessments and real-time monitoring. Engaging stakeholders and fostering a security-aware culture are crucial steps in embedding the standard's principles across your organisation.
By prioritising ISO 27001:2022, you not only safeguard your organisation's data but also drive strategic advantages in a competitive market.
How Does ISO 27001:2022 Enhance Security Frameworks?
Key Strategies for Threat Mitigation
- Conducting Risk Assessments: Thorough evaluations identify vulnerabilities and potential threats (ISO 27001:2022 Clause 6.1), forming the basis for targeted security measures.
- Implementing Security Controls: Annex A controls are utilised to address specific risks, ensuring a holistic approach to threat prevention.
- Continuous Monitoring: Regular reviews of security practices allow adaptation to evolving threats, maintaining the effectiveness of your security posture.
Data Protection and Privacy Alignment
ISO 27001:2022 integrates security practices into organisational processes, aligning with regulations like GDPR. This ensures that personal data is handled securely, reducing legal risks and enhancing stakeholder trust.
Building a Proactive Security Culture
By fostering security awareness, ISO 27001:2022 promotes continuous improvement and vigilance. This proactive stance minimises vulnerabilities and strengthens your organisation's overall security posture. Our platform, ISMS.online, supports these efforts with tools for real-time monitoring and automated risk assessments, positioning your organisation as a leader in information security.
Incorporating ISO 27001:2022 into your security strategy not only fortifies defences but also enhances your organisation's reputation and competitive advantage.
What Advantages Does ISO 27001:2022 Offer to CEOs?
ISO 27001:2022 is a strategic asset for CEOs, enhancing organisational resilience and operational efficiency through a risk-based methodology. This standard aligns security protocols with business objectives, ensuring robust information security management.
How Does ISO 27001:2022 Enhance Strategic Business Integration?
- Risk Management Framework: ISO 27001:2022 provides a comprehensive framework for identifying and mitigating risks, safeguarding your assets, and ensuring business continuity.
- Regulatory Compliance Standards: By aligning with global standards like GDPR, it minimises legal risks and strengthens governance, essential for maintaining market trust.
What Are the Competitive Advantages of ISO 27001:2022?
- Reputation Enhancement: Certification demonstrates a commitment to security, boosting customer trust and satisfaction. Organisations often report increased client confidence, leading to higher retention rates.
- Global Market Access: With acceptance in over 150 countries, ISO 27001:2022 facilitates entry into international markets, offering a competitive edge.
How Can ISO 27001:2022 Drive Business Growth?
- Operational Efficiency: Streamlined processes reduce security incidents, lowering costs and improving efficiency.
- Innovation and Digital Transformation: By fostering a culture of security awareness, it supports digital transformation and innovation, driving business growth.
- Reputation Enhancement: Certification demonstrates a commitment to security, boosting customer trust and satisfaction. Organisations often report increased client confidence, leading to higher retention rates.
- Global Market Access: With acceptance in over 150 countries, ISO 27001:2022 facilitates entry into international markets, offering a competitive edge.
How Can ISO 27001:2022 Drive Business Growth?
- Operational Efficiency: Streamlined processes reduce security incidents, lowering costs and improving efficiency.
- Innovation and Digital Transformation: By fostering a culture of security awareness, it supports digital transformation and innovation, driving business growth.
Integrating ISO 27001:2022 into your strategic planning aligns security measures with organisational goals, ensuring they support broader business objectives. Our platform, ISMS.online, simplifies compliance, offering tools for real-time monitoring and risk management, ensuring your organisation remains secure and competitive.
How to Facilitate Digital Transformation with ISO 27001:2022
ISO 27001:2022 provides a comprehensive framework for organisations transitioning to digital platforms, ensuring data protection and adherence to international standards. This standard is pivotal in managing digital risks and enhancing security measures.
How to Manage Digital Risks Effectively
ISO 27001:2022 offers a risk-based approach to identify and mitigate vulnerabilities. By conducting thorough risk assessments and implementing Annex A controls, your organisation can proactively address potential threats and maintain robust security measures. This approach aligns with evolving cybersecurity requirements, ensuring your digital assets are safeguarded.
How to Foster Secure Digital Innovation
Integrating ISO 27001:2022 into your development lifecycle ensures security is prioritised from design to deployment. This reduces breach risks and enhances data protection, allowing your organisation to pursue innovation confidently while maintaining compliance.
How to Build a Culture of Digital Security
Promoting a culture of security involves emphasising awareness and training. Implement comprehensive programmes that equip your team with the skills needed to recognise and respond to digital threats effectively. This proactive stance fosters a security-conscious environment, essential for successful digital transformation.
By adopting ISO 27001:2022, your organisation can navigate digital complexities, ensuring security and compliance are integral to your strategies. This alignment not only protects sensitive information but also enhances operational efficiency and competitive advantage.
What are the Key Considerations for Implementing ISO 27001:2022
Implementing ISO 27001:2022 involves meticulous planning and resource management to ensure successful integration. Key considerations include strategic resource allocation, engaging key personnel, and fostering a culture of continuous improvement.
Strategic Resource Allocation
Prioritising tasks based on comprehensive risk assessments is essential. Your organisation should focus on high-impact areas, ensuring they receive adequate attention as outlined in ISO 27001:2022 Clause 6.1. Utilising platforms like ISMS.online can automate tasks, reducing manual effort and optimising resource use.
Engaging Key Personnel
Securing buy-in from key personnel early in the process is vital. This involves fostering collaboration and aligning with organisational goals. Clear communication of the benefits and objectives of ISO 27001:2022 helps mitigate resistance and encourages active participation.
Fostering a Culture of Continuous Improvement
Regularly reviewing and updating your Information Security Management Systems (ISMS) to adapt to evolving threats is crucial. This involves conducting periodic audits and management reviews to identify areas for enhancement, as specified in ISO 27001:2022 Clause 9.3.
Steps for Successful Implementation
To ensure successful implementation, your organisation should:
- Conduct a gap analysis to identify areas needing improvement.
- Develop a comprehensive project plan with clear objectives and timelines.
- Utilise tools and resources, such as ISMS.online, to streamline processes and enhance efficiency.
- Foster a culture of security awareness through regular training and communication.
By addressing these considerations, your organisation can effectively implement ISO 27001:2022, enhancing its security posture and ensuring alignment with international standards.
Get an 81% headstart
We've done the hard work for you, giving you an 81% Headstart from the moment you log on.
All you have to do is fill in the blanks.
Book a Demo with ISMS.online
Start your ISO 27001:2022 journey with ISMS.online. Schedule a personalised demo now to see how our comprehensive solutions can simplify your compliance and streamline your implementation processes. Enhance your security framework and boost operational efficiency with our cutting-edge tools.
How Can ISMS.online Streamline Your Compliance Journey?
- Automate and Simplify Tasks: Our platform reduces manual effort and enhances precision through automation. The intuitive interface guides you step-by-step, ensuring all necessary criteria are met efficiently.
- What Support Does ISMS.online Offer?: With features like automated risk assessments and real-time monitoring, ISMS.online helps maintain a robust security posture. Our solution aligns with ISO 27001:2022's risk-based approach, proactively addressing vulnerabilities (ISO 27001:2022 Clause 6.1).
- Why Schedule a Personalised Demo?: Discover how our solutions can transform your strategy. A personalised demo illustrates how ISMS.online can meet your organisation's specific needs, offering insights into our capabilities and benefits.
How Does ISMS.online Enhance Collaboration and Efficiency?
Our platform fosters seamless teamwork, enabling your organisation to achieve ISO 27001:2022 certification. By utilising ISMS.online, your team can enhance its security framework, improve operational efficiency, and gain a competitive edge. Book a demo today to experience the transformative power of ISMS.online and ensure your organisation remains secure and compliant.