
How to develop an asset inventory for ISO 27001
Table Of Contents:
Introducing Asset Inventory
You have to create an inventory of your organisation’s information assets to:
- Build an effective Information Security Management System (ISMS)
- Achieve ISO 27001 compliance or certification
When we talk about information assets we find that most people think about things like laptops and servers. But there are many other items you’ll need to consider. People, intellectual property and even intangible assets like your organisation’s brand can all fit into your Asset Inventory.
Once you’ve developed your Asset Inventory your next step is to undertake three exercises:
- Filtering
- Prioritisation
- Categorisation
Then you’ll need to map the risk to your assets by using those categories you’ve just identified.
Developing your Asset Inventory can seem quite complicated at first. But if you’re using ISMS.online you don’t really need to know the ins and outs before you get started.
If this is your first ISO 27001 implementation, you’ll benefit greatly from our Virtual Coach feature. This series of videos is available 24/7 within the platform. It guides you through your certification journey, including developing your Asset Inventory.
What should be included in an ISO 27001 asset inventory?
The 2013 version of the information security standard introduced a distinct change to the ISO 27001 requirements which now expect all information assets to be considered rather than simply physical assets. This includes anything of value to the organisation where information is stored, processed and accessible, but it is the information that is of real interest, less so the network or device per se, although clearly they are still assets and need to be protected:
- Information (or data)
- Intangibles – such as IP, brand and reputation
- People – Employees, temporary staff, contractors, volunteers etc
And the physical assets associated with their processing and infrastructure:
- Hardware – Typically IT servers, network equipment, workstations, mobile devices etc
- Software – Purchased or bespoke software
- Services – The actual service provided to end-users (e.g. database systems, e-mail etc)
- Locations & Buildings – Sites, buildings, offices etc
Any type of asset can be grouped together logically according to a number of factors such as:
- Classification – e.g. public, internal, confidential etc
- Information type – e.g. personal, personal sensitive, commercial etc
- Financial or non-financial value
An auditor will expect to see an inventory, or inventories, that cover all the relevant assets within the scope of the ISMS. Each asset must be assigned an owner and each must be assigned a classification.
Who should the asset owner be and what are their ISO 27001 responsibilities?
The owner is not necessarily the legal or physical holder of the asset but the person that has the responsibility and matching authority to ensure that, at a minimum:
-
- Assets are inventoried;
- Assets are correctly classified and protected;
- Access restrictions to the asset and its classification are periodically reviewed; and
- Assets are handled correctly when being deleted or destroyed.
Day-to-day responsibilities for asset management (e.g. updating the inventories, carrying out audits etc) can be delegated but the ultimate responsibility for ensuring correct management remains with the relevant asset owner.
It is the asset owner who is responsible for setting the protection requirements for the asset, such as access restriction, in line with organisational policies and standards.
How does the ISO 27001:2013 asset inventory relate to GDPR?
To comply with the General Data Protection Regulation (GDPR) an organisation must keep an inventory of systems that hold and process personally_identifiable_information”>personal information. It also requires that the risks surrounding personal data are identified, assessed and treated, so following the ISO 27001:2013 approach to assets and risks assessment means it can easily encompass and be aligned to incorporate the GDPR requirements too.
Should you use a template or tool to manage your asset inventory?
There are many example templates for asset inventories/registers available and these follow a simple spreadsheet approach which are just as easy to build yourself.
However, a spreadsheet is a static document and whilst they are great for financial modelling and basic stuff, they are not so good for demonstrating how the asset links to the identified risks, the relevant policies and controls, or the other dynamic work of an information security management system.
A good technology tool for asset inventories will come pre-configured, with the option to customise to suit your own classifications, allow you to assign owners, due dates and reminders and to capture all the evidence required in one secure location.
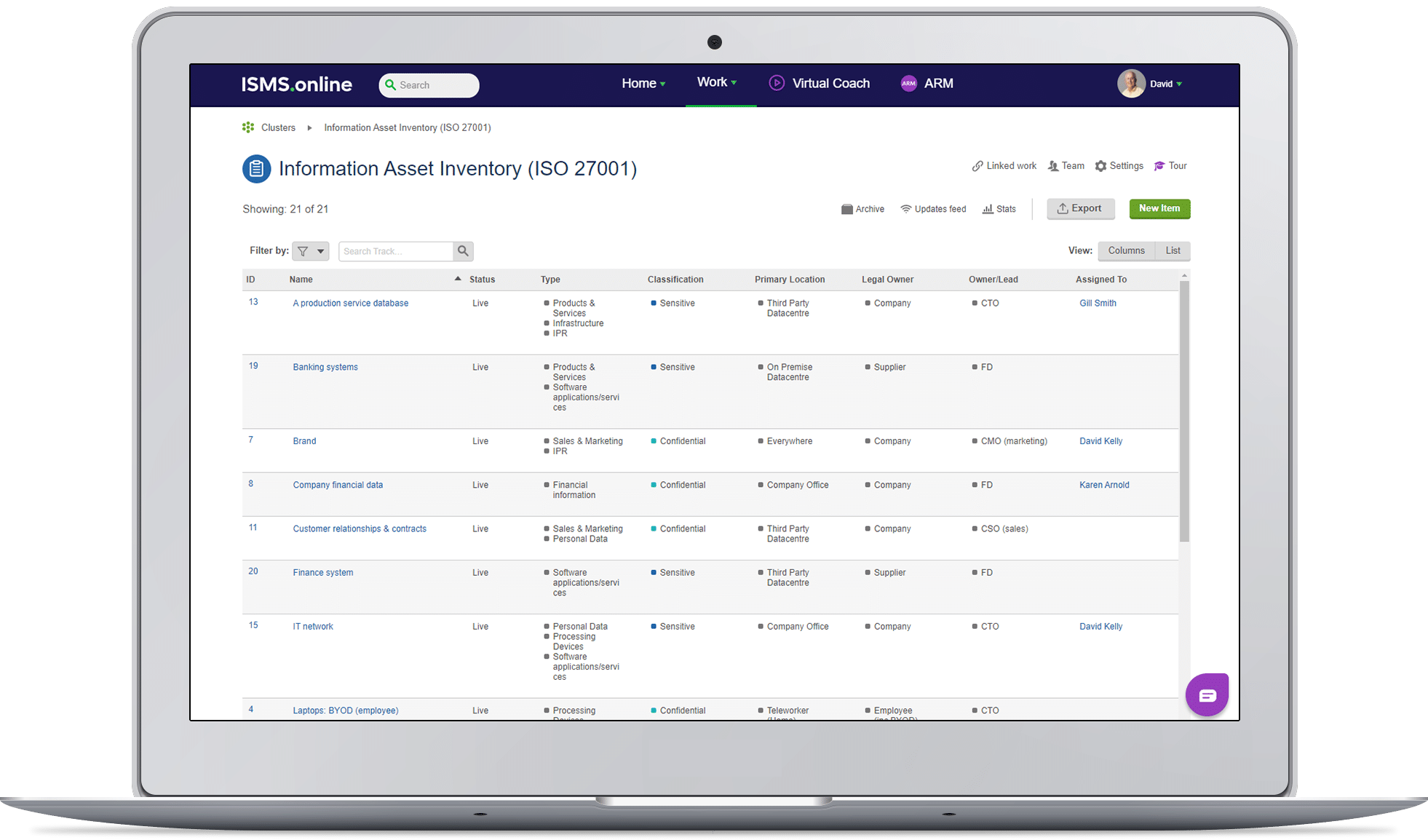
Also consider an information security management tool that allows you to assign values to your assets as this will help you prioritise risk assessments and understand any potential impact of incidents, events or breaches.
Finally, the best tools will come with the ability to easily link the asset to risks on your risk treatment plan, to your ISMS controls, supply chain and any other actions in the ISMS that demonstrate your assets are well protected.
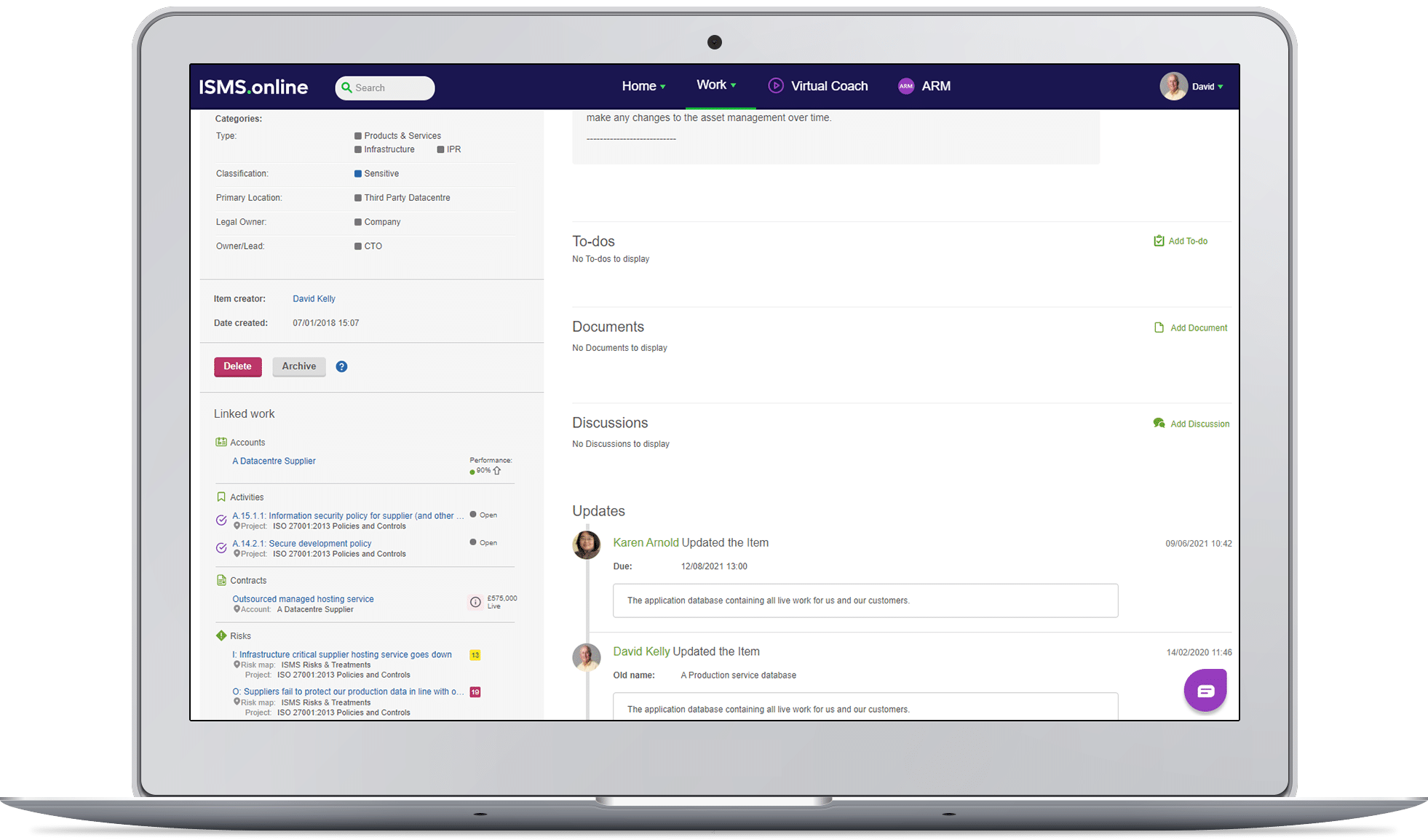
In fact, in ISMS.online, using this same powerful linking will take you on a simple journey from information asset, to risk, to the controls needed in the treatment of the risk and then, dynamically from the control to updating the Statement of Applicability with the justification for its implementation. It really is that simple with ISMS.online.
So, building your own asset spreadsheet may have no perceived cost but will have the challenge of much higher management and coordination with the other parts of the ISMS, especially if you are aiming for ISO 27001 certification. Or you can take a longer-term view and invest in a specialist asset management tool. But they’re often complex and detail heavy. Information asset management could well become a full-time job in its own right. And you’ll still need to link your tool with the rest of your ISMS.
Instead of reaching for a spreadsheet or a stand-alone specialist tool, we’d recommend looking for an ISMS platform that includes its own asset inventory tool. It should:
- Come pre-configured, but be easy to customise with your own classifications
- Let you assign asset owners, and asset management due dates and reminders
- Dynamically capture evidence for internal and external audits in one secure location
It should also let you assign values to your assets. That’ll help you prioritise risk assessments and assess the potential impact of any security incidents, events or breaches. And you should be able to link through to your risk treatment plan and beyond.
That’s the kind of linking ISMS.online lets you do. You can move from an information asset, to a risk it faces and to the control that treats that risk. Then you can jump from that control to your Statement of Applicability, updating it with the justification for its implementation.
It really is that simple.




