
Resources
SOC 2 Hub
A comprehensive digital content hub offering in-depth information on SOC 2 standard, what it is, and how to achieve it.
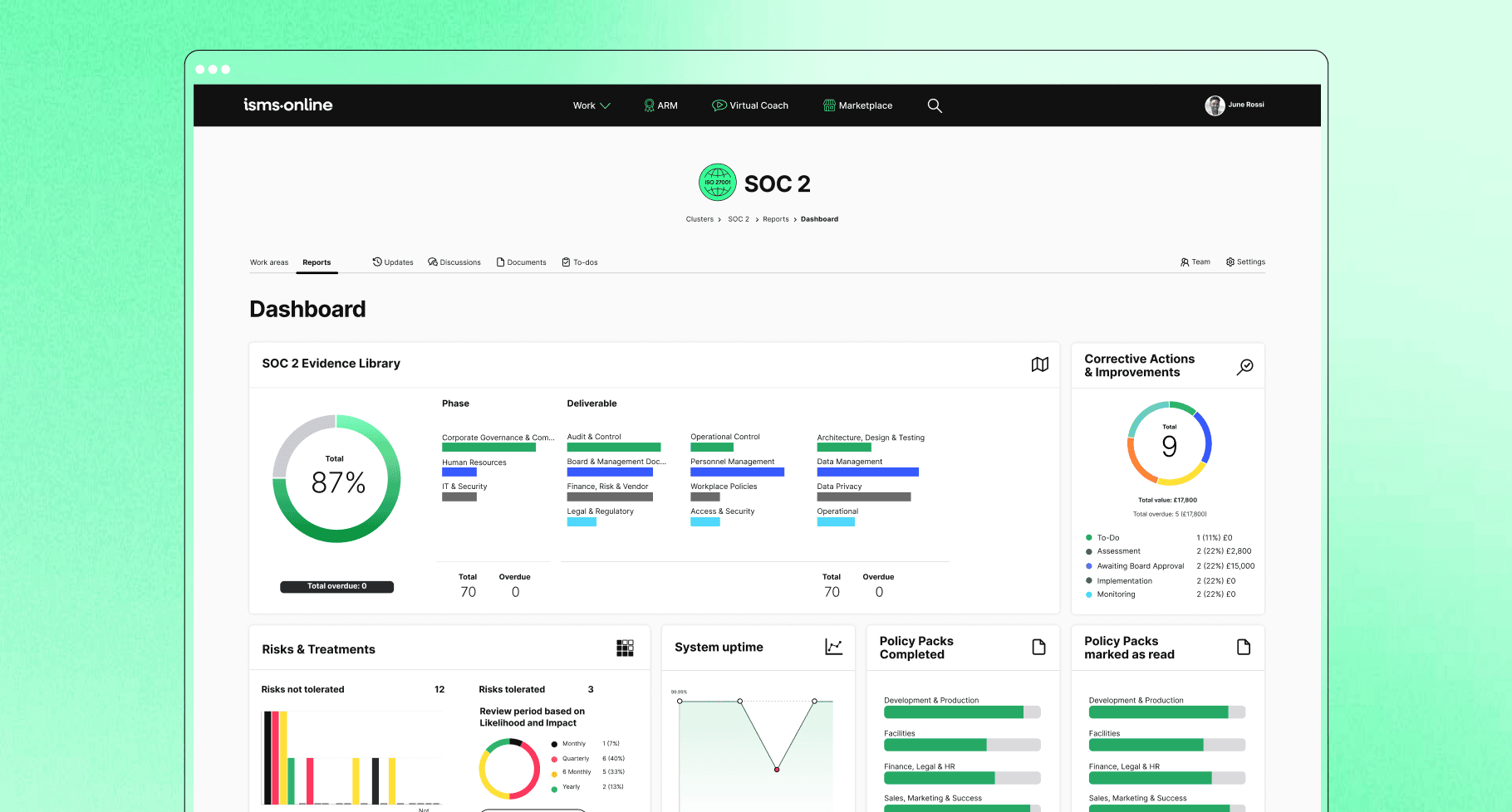
Achieve SOC 2 with confidence
IO gives you all the tools you need to achieve SOC 2 in one powerful platform. Including pre-written policies, built-in risk map and a comprehensive evidence library, as well as our first-class support team with you every step of the way.
Achieving SOC2 with IO

Your guide to achieving SOC 2 compliance
Cut through the complexity of SOC 2 compliance with this practical, step-by-step guide. Discover how to achieve audit success and build long-term trust without the stress or wasted time.

Behind the SOC 2 Report: What auditors, MSPs & platforms wish you knew
Get a 360° view of SOC 2, exploring what each stakeholder expects, where businesses often get stuck, and how to build a right-sized SOC 2 program that delivers results, without taking shortcuts that cost you in the long run.

Headstart: Begin with 81% of the work already complete
Up to 81% of the work is already done for you thanks to Headstart, our pre-built bank of SOC 2 tools, frameworks, policies & controls, and more. No wrong turns, no rabbit holes, just a direct path to SOC 2 success.

SOC 2, step-by-step
The Assured Results Method is your simple, practical, time-saving path to SOC 2 success. Broken into 11 steps, just run through the process one step at a time, and you’ll be attested before you know it.

Your in-platform guide to SOC 2
Created by our in-house SOC 2 experts, Virtual Coach delivers simple, practical advice whenever and wherever you need it, giving you the confidence that you’re on the right path to certification success.
Take a deeper dive
Understanding the value of SOC 2 compliance for your company
SOC 2 shifts compliance from a static checklist to a proactive, value-generating system that supports long-term resilience. In this article we’ll take a deep dive into how it can transform security and trust into a measurable business advantage.
Is SOC 2 a certification? Spoiler – no it’s not
SOC 2 is not a traditional certification, but a continuous compliance framework that transforms static, checklist-based audits into a proactive validation process. In this article we’ll explore how it differs from other standards, and what that means for you.
Why your company should get SOC 2 attested
Wondering if SOC 2 attestation is worth it? This guide explores the real benefits — from proving security to building customer trust — and why achieving attestation can be a strategic advantage, not just a compliance exercise.
How to get a SOC 2 attestation
This article shows how SOC 2 attestation works: engaging a CPA auditor, mapping controls to Trust Services Criteria, collecting continuous evidence, and maintaining operational effectiveness. It’s not a static certification—it’s proving your controls stay compliant over time.
What is a SOC 2 Type II report – timelines, evidence & takeaways
Discover what every organization needs to know about SOC 2 Type II reports
SOC 2 attestation letter – what it is and how to use it
A SOC 2 attestation letter is a formal document that verifies an organisation’s internal controls align with Trust Services Criteria, providing verifiable proof of compliance and audit readiness.
All about audits
Your guide to SOC 2 audits – how they work and what’s required
Preparing for a SOC 2 audit can feel complex. This guide explains the process, key requirements, and practical steps to streamline evidence gathering, reduce stress, and turn SOC 2 compliance into an ongoing business advantage.
Are you actually ready for attestation?
True SOC 2 readiness means more than having policies – it’s about continuously validated controls, clear evidence chains against trust criteria, and a system that uncovers gaps before audit time. Here’s how to avoid surprises.
How long does a SOC 2 audit take?
SOC 2 audit timing depends on readiness, control maturity, and documentation quality. This guide outlines the phases—from planning through reporting—and the main factors that stretch or shorten the schedule, so you can plan with confidence.
How to scope your SOC 2 audit
Scoping a SOC 2 audit means defining what systems, services, and controls are reviewed. This guide helps you choose the right trust criteria, determine in-scope assets, and limit scope creep so audit costs, time and risk stay manageable.
How to choose the right SOC 2 auditor
Choosing the right SOC 2 auditor is crucial. This guide helps you evaluate credentials, methodology, experience, and cross-framework expertise to ensure rigorous control-to-evidence mapping, reduce audit risk, and maximise transparency and operational efficiency.
SOC 2 audit for small businesses and startups – what to expect
Even small businesses and startups can use SOC 2 audits to show strong risk management and build credibility. This guide explains what a SOC 2 involves, how to prepare with limited resources, and what stakeholders expect.
Best of the blog

Demystifying SOC 2 compliance: A comprehensive guide for businesses
Understanding SOC 2 compliance can all be overwhelming. Fear not! In this blog, we’ll unravel the mysteries surrounding SOC 2 compliance. We’ll break down the definitions, demystify its purpose, and guide you through the necessary steps to achieve and maintain SOC 2 compliance.

Your fast-track to seamless compliance
For SaaS providers, cloud-based businesses, and companies handling customer data, SOC 2 compliance isn’t just about meeting an industry standard—it’s a competitive differentiator.
ISO 27001 certification vs SOC 2 attestation
Trying to decide if you should adopt ISO 27001 or SOC 2? Here we’ll provide an ISO 27001 vs SOC 2 comparison, including what they are, what they have in common, which is suitable for your organisation, and why.
SOC 2 by business size

Get compliant. Build credibility. Grow your business.
You don’t need a compliance team to nail your compliance. Our founder-friendly platform has everything you need to get you certified fast.

Compliance confidence for small businesses
Meet your clients regulatory requirements without slowing down or breaking the bank. IO helps you move fast, while staying secure.

Professional compliance, bigger deals
As your business scales, your compliance needs to scale with you. IO takes the mystery out of compliance, making it easy to impress your clients.

Resilient compliance for established companies
Your compliance needs to scale with your business, but that’s not an easy process. You need a platform that can keep up.
Compliance confidence for enterprise
Meet your clients regulatory requirements without slowing down or breaking the bank. IO helps you move fast, while staying secure.
Customer stories
SOC 2 Trust Services Criteria (TSC)
Breakdown across Security (Common Criteria CC1–CC9)
Common Criteria – Control Environment (CC1.1–CC1.5)
CC2 Information & Communication (CC2.1–CC2.3)
CC3 Risk Assessment (CC3.1–CC3.4)
CC4 Monitoring (CC4.1–CC4.2)
CC5 Control Activities (CC5.1–CC5.3)
CC6 Logical & Physical Access (CC6.1–CC6.8)
CC7 System Operations (CC7.1–CC7.5)
CC8 Change Management (CC8.1)
CC9 Risk Mitigation (CC9.1–CC9.2)
Availability (A1.x)
Processing Integrity (PI1.x)
Confidentiality (C1.x)
Privacy (P Series P1.0–P8.1)
P1.0 Privacy P1.0 Explained
P1.1 Privacy P1.1 Explained
P2.0 Privacy P2.0 Explained
P2.1 Privacy P2.1 Explained
P3.0 Privacy P3.0 Explained
P3.1 Privacy P3.1 Explained
P3.2 Privacy P3.2 Explained
P4.0 Privacy P4.0 Explained
P4.1 Privacy P4.1 Explained
P4.2 Privacy P4.2 Explained
P4.3 Privacy P4.3 Explained
P5.1 Privacy P5.1 Explained
P5.2 Privacy P5.2 Explained
P6.0 Privacy P6.0 Explained
P6.1 Privacy P6.1 Explained
P6.2 Privacy P6.2 Explained
P6.3 Privacy P6.3 Explained
P6.4 Privacy P6.4 Explained
P6.5 Privacy P6.5 Explained
P6.6 Privacy P6.6 Explained
P6.7 Privacy P6.7 Explained
P7.0 Privacy P7.0 Explained
P7.1 Privacy P7.1 Explained
P8.0 Privacy P8.0 Explained
P8.1 Privacy P8.1 Explained
About SOC 2
Take a virtual tour
Start your free 2-minute interactive demo now and see
ISMS.online in action!










