
Information Security Risk Management Explained – ISO 27001
Table Of Contents:
Risk management is an often used phrase in business today. However without having a consistent interpretation of what it means and how to do it effectively, that creates risk in itself!
Information security risk management and cybersecurity risk management are derivatives of that too. Both of these risk areas are growing in importance to organisations so the purpose of this article is to help demystify it to a practical and actionable level. In particular, we’ll share how to do risk management for the ISO 27001 standard and achieving compliance for the risk-focused part of the General Data Protection Regulation (EU GDPR).
What is information security risk management?
Unsurprisingly it means different things to different people. Before I share my thoughts, it’s worth quickly going back to basics on risk management and building from there.
ISO 31000:2018 is a recently updated version of the International Standards Organisation (ISO) standard for risk management that defines risk as “the effect of uncertainty on objectives”.
Risk management is therefore about decision making and taking actions to address uncertain outcomes, controlling how risks might impact the achievement of business goals.
Why risk management is important in information security
Information security risk management (ISRM) is the process of identifying, evaluating, and treating risks around the organisation’s valuable information. It addresses uncertainties around those assets to ensure the desired business outcomes are achieved.
There are different ways to manage risk and we will cover some of those off later in the article. One size does not fit all and not all risk is bad…risks do create opportunities too, however the most of the time it is threat focused.
Why ‘joined up’ risk management is important
If I asked you to bet (invest) on something happening e.g. Liverpool beating Manchester United at football, you’d probably consider a number of things. Past history, current form, injuries, game venue and so on. You’d also have your own bias (e.g. being a Liverpool fan and eternal optimist) and appetite for taking the risk (e.g. how much of your salary to bet on the win). My view on the investment needed and outcome expected versus yours may be very different, although we could both be looking at the same information.
The challenge is not that different in organisations, however, it is normally complicated by many more people being involved in work initiatives, each with their own history, bias, risk appetite etc. In fact, many people are experienced in their own way towards risk management and have implicitly overlayed their own methodology and probably also created their own tools. Hands up if you’ve ever created a risk register as part of a work project; did you do it in a document or spreadsheet and put your own process into the evaluation and actions? We’ve been there!
That is a good start towards calculated risk management. When it comes to meeting regulations like GDPR and standards like ISO 27001 for information security management there are specific things to describe and demonstrate. These include:
- Alignment of risk management actions with business objectives
- A consistent and repeatable methodology to ‘show your working’ and ensure it can be applied in line with the standards and regulations (which we’ll cover more of shortly)
Doing this is going to help you run a better business. It will help deal with those uncertainties as you’ll be better informed on the actions to take. Done well it will also act as an insurance mechanism in the event that something did go badly wrong and you suffered a data breach around personal data. The Information Commissioner (as Supervisory Authority for the UK in applying GDPR fines) would take that information security risk management process into account when considering any penalties or enforcement actions.
So, not only is risk management important, joined-up risk management that takes a business objectives led approach to any investment or action is crucial. And that’s for any type of risk, whether it be quality, environmental, health, or cyber and information security.
So lets align on those latter topics of cybersecurity and information security, then look deeper at the risk management methodology and approach for ISO 27001 and Europe’s General Data Protection Regulation (GDPR).
Are cybersecurity and information security different?
Yes. Cyber is a recent addition to management vocabulary. In fact, it is only just over 30 years ago that the Morris worm was considered as one of the earliest cyber threats.
However, the hype and consequences of poor cybersecurity continue to grow exponentially now as the world is ever more digital and electronic. Serious Organised Crime Groups (OCG’s) are looking beyond traditional crime to exploit those cyber vulnerabilities.
With massive fines from personal data breaches as well, GDPR has also raised the bar on reasons to tighten up your whole infrastructure.
Cybersecurity and information security are commonly considered to be the same thing, but they are not. Without having a deeply theoretical or academic debate, cybersecurity is more typically about the protection of information held electronically. That means it’s a subset of a broader information security posture, which looks at the protection of information from all angles.
Information security also means physical security (e.g. locks on doors) as well as people based (e.g. when a key person in the organisation leaves – or is ill – with all the knowledge in their head. What steps are taken to keep that asset protected from use if they leave – or making it available if they are off sick).
In ISO 27000, information security is defined as: “The preservation of confidentiality, integrity, and availability of information.” Implicitly this includes cyber. International Standards like ISO 27001 and GDPR also expect you to consider information security in its more holistic sense.
Cyber Essentials looks more specifically at some of the high-risk control areas that would help prevent cyber-based losses. Cyber Essentials is complementary to ISO 27001 and GDPR. It is a good foundation to build on for smaller businesses who are reliant on digital services.
Cybersecurity is also commonly presumed to be about the external threats getting in, however cyber problems can occur internally too. Access control, physical protection should all be there for internal as well as external threat management.
Some people also see IT security synonymously with information security too but in my opinion, that is unlikely, without being clear on the bigger picture below and a more strategic, holistic role for IT (or any other 2 or 3 letter dept acronym).
One of the dangers in ‘only’ thinking about cybersecurity risk management is that it does get left to the people with the IT skills. It’s the same with physical security being left to the facilities management department, or other people issues (as per the example above about leaving or illness) solely being left with human resources (HR).
Don’t get me wrong, they are key stakeholders. However, without a business led joined-up approach to information security risk management there is a possibility of getting the wrong solutions in place. It could then create more risk and cost, especially if staff and supply chain don’t embrace the policies and controls, or find them too painful to follow, with multiple and sometimes conflicting hoops to jump through.
What’s more important is clarifying the role and scope of your (IT) team and being clear how integrated into the business objectives they are (or not) along with the influence they hold on decision making.
It is the same for other departments too regardless of the sign above the door. We often say that it’s not about information security, it’s about doing business securely; and that makes it everyone’s responsibility. You do need clear leadership and accountability though to have a chance of achieving an ISO 27001 certification.
ISO 27001 is actually great for helping an organisation go through a structured approach, working from its purpose, issues, interested parties, scope, information at risk etc. In that process, you will identify who should be involved. Spoiler – it will be more than just the IT team and it will cover more than just cyber!
Risk management methodology
Article 32 of the EU General Data Protection Regulation explicitly states that an organisation needs to risk assess using Confidentiality, Integrity and Availability (CIA). This also neatly dovetails with ISO 27001 because that CIA approach is expected there too. As such you can use one approach to information security risk management for all your information assets, not just personal data.
-
Confidentiality: information is not made available or disclosed to unauthorised individuals, entities or processes
-
Integrity: safeguarding the accuracy and completeness of information assets
-
Availability: being accessible and usable upon demand by an authorised entity
The CIA of information security underpins everything else you do in your risk assessment and helps informs the steps taken thereafter. In starting to evolve your methodology for information security risk management, one of the often looked over issues is conflicts and priorities in addressing CIA based risk.
For example, what happens if a data breach (confidentiality) occurs? Do you then take your services offline or keep them up (availability issue)? If you are aiming to obtain UKAS ISO 27001 certification the external auditor will expect to see how you deal with conflicts and priority risks in your documentation. It’s a point of detail that needs consideration, but let’s first summarise all the core areas you’ll want to (briefly but clearly) document in your risk methodology.
What are the 5 steps in a risk management process?
Let’s assume your goal is to obtain ISO 27001 certification, whilst complying with GDPR. We’ll craft our information security risk methodology with that in mind.
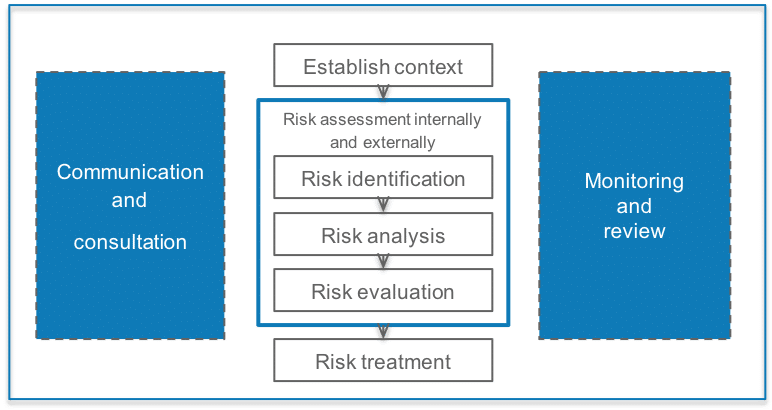
1. Risk identification
The first step in the risk management process is to identify the risk. The source of the risk may be from an information asset, related to an internal/external issue (e.g. associated to a process, the business plan etc) or an interested party/stakeholder related risk.
2. Risk analysis
Once you know the risks, you need to consider the likelihood and impact (LI) to allow you to distinguish between (say) low likelihood and low impact, versus higher ones.
3. Risk evaluation
After analysing the risk, you can then prioritise investments where needed the most, and conduct reviews based on the LI positioning. You have to document what each position means so that it can be applied by anyone following the method. We use a 5 x 5 grid system in our easy to follow information security risk management tool within ISMS.online. (Tip: It also includes a risk bank with popular risks and treatments too, saving huge amounts of time).
The criteria includes a range from very low to very high for likelihood. It has an explanation of what that means e.g. very low is no history of occurrence and would need specialist skills and high investment to occur. Impact criteria range from very low with insignificant consequences and costs, all the way up to very high being almost certain death of the business. You get the picture. Its not hard, just needs clarity and documenting; otherwise my 3×4 might be different to yours and we end up back where we started at the top of the page.
4. Risk treatment
Treatment of the risk, which is also known as ‘risk response planning’ must include the evidence behind the risk treatment.
In simple terms ‘risk treatment’ can be work you are doing internally to control and tolerate the risk, or it could mean steps you are taking to transfer the risk (e.g. to a supplier), or it could be to terminate a risk entirely.
ISO 27001 is great here too because the Standard also gives you an Annex A set of control objectives to consider in that treatment, which will form the backbone of your Statement of Applicability. The Annex A controls also give you an opportunity to look ‘bottom-up’ and see whether it triggers risks you may not have thought about before too.
5. Monitor and review the risk
The first part of the monitor and review stage of the risk management process is to describe your processes for monitoring and review. This can be broken into the following areas:
-Staff engagement and awareness
Get appropriate staff involved in the process regularly and have a forum to give and receive feedback.
You must have an owner for each risk so you might look to delegate that down to the front (first) line as per the broadly recognised ‘3 lines of defence’ model.
– Management reviews
Risk reviews are a standard part of that 9.3 agenda and you might decide to have risk owners at this level instead, delegating operational work down to line 1 but retaining ownership.
Your management reviews have to be at least annual, (we encourage far more regular ones) but they might not be long enough to drill into each risk and cover everything else on that agenda too. As such we also recommend a process where the risk owner is tasked to review the review based on its grid position e.g. monthly review for a very high likelihood and very high impact risk, whereas annually is fine for reviewing a very low likelihood and very low impact risk. You then show your auditor that those risk reviews are pragmatic, based on the impact and likelihood, which they like.
– Improvement
Internal audits and use of the other mechanisms in clause 10 around improvement can be nicely associated with the more strategic risk review process too.
Risk management requirements of ISO 27001:2013/17
There are 2 main requirements where risk management is expressed: Clause 6 Planning and Clause 8 Operation.
Clause 8 is simply about implementing and operating what you have described for 6.1 so let’s concentrate on 6.1 here knowing that you have to live and breathe it in practice (8) to have a chance of running the business well and obtaining certification.
Clause 6.1: Actions to address risks and opportunities
Let’s also remember that this process needs to be business objectives led (i.e. establish context above) so you need to show the information security management system can:
- achieve the intended outcomes
- prevent, or reduce the undesired effects
- achieve continual improvement
If you are taking a top-down approach, earlier in the ISO requirements you’ll have considered the context and purpose of your organisation with the issues facing it (4.1), interested parties (4.2), scope (4.3), information assets etc, which is illustrated in the image below (this is an extract from our ISO 27001 Virtual Coach programme within ISMS.online. This is the most logical approach to take.)
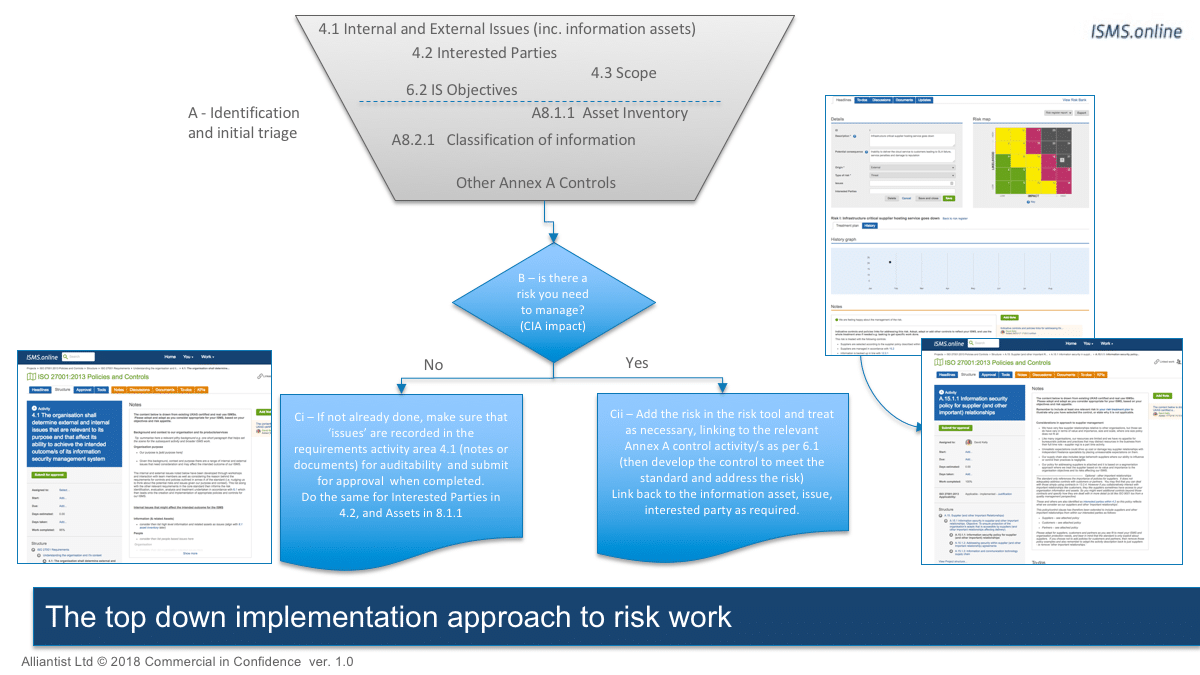
The organisation has to plan how to address the risks threats and opportunities. ISO 27001 is also very interested in:
- How the risks integrate into the wider information security management system
- How actions are taken, and evaluating the effectiveness of the actions taken on the way
As with the example above about risk prioritisation and conflict, there is a bit more detail too. 6.1 also includes a need to document risk acceptance criteria for performing risk assessments and how those all produce consistent, valid and comparable results around the CIA of information assets in scope.
An external auditor will expect to see a methodology that explains all these things well and have increased confidence for seeing how easily the ISMS operates in a joined-up fashion. It’s a thing of beauty when your information assets link nicely to the risks and they, in turn, connect to the policies and controls being used to address them!
If you like researching this area (and have lots of time and money) you could also purchase standards for ISO 27005 and ISO 31000 to really delve deeply into these topics……then again…….
Whatever you do, make sure it’s practical & actionable in line with your business goals.
Do not overwhelm the resources that will manage it (especially if they have another day job), as it won’t get done and you’ll be in trouble.
It’s no good coming up with a very sophisticated monte carlo simulation method and complex algorithms to calculate risk and be a full-time role if you don’t need it. Equally, just dropping some risks in a document without a method for analysis, action, and monitoring is unlikely to satisfy your business decision-making need, and won’t wash with an external auditor during certification.
In bringing all this alive you’ll probably explain the methodology with simple text and pictures. Then to actually manage information security risk operationally you’ll also need a tool to get the job done.
Should you build your own information security risk management tool?
Anyone competent with spreadsheets has the ability to create their own risk register and it is a popular choice especially for organisations that are new to ISO 27001 or can’t afford (or really don’t need) some of the heavyweight standalone risk tools on the market.
Challenges with both approaches
Spreadsheets and documents include:
- Perceived as free and whilst the time it takes to initially build a tool is relatively quick, managing it over time is increasingly painful as the ISMS matures
- Linking to information assets and controls/policies in use is clunky, pointing to other systems at best, at worst not evidencing at all
- Documenting work done around the risk with its movement over time to see investments are working is not easy (especially in one excel field)
- Setting tasks and reviews/reminders is not possible so it means another job to schedule somewhere else
- Version control is hard work and not easy to quickly see earlier history. Its a nightmare if multiple versions are held locally too by different stakeholders
- Gets complicated with lots of risks and visualisation is not always easy to get to the signal from the noise
- Good for the person who built it but not always easy for others to build on or use
Expert risk management solutions that standalone include:
- Can be expensive to acquire and need lots of customisation or consulting before use
- Can take lots of training – feeding a beast and sometimes missing the point of risk management for busy professionals who are not full-time risk managers
- Don’t always link up with the broader ISMS, meaning rework or use of multiple systems – worst case outcome is that the standalone tool conflicts with other systems you have purchased – not necessarily at the point of purchase but as the application providers add or change features
These thoughts are based on our own experiences and customers we worked with in the early days of building ISMS.online as an all in one place ISMS. We also cover the 10 characteristics behind an ISMS as part of our business plan whitepaper so if you want to learn more about investing in a tool, download that here.
If building security software is not your core competence and you are serious about information security risk management without breaking the bank to achieve it, then book a demo for ISMS.online now. It’s great if you want something all in one place out of the box which is ready to adopt and help fast track towards ISO 27001 as well as GDPR risk management compliance.




